Note:
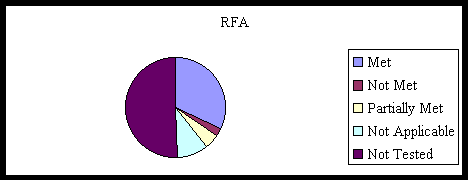
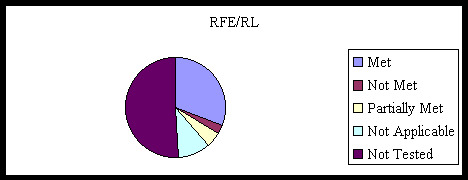
Based upon the Visual Comparison of the SRTM results, there is no comparative difference in security posture between RFA and RFE/RL.
Source SRTM Appendix A
MUTUAL INFORMATION SECURITY TEST AND EVALUATION
MISST&E
REPORT
Version 1.0
March 2003
by
Flint
Enterprises Incorporated
7653 North Station East, Arlington, Virginia
Prepared for
Radio Free Asia
TABLE OF CONTENTS
1 EXECUTIVE SUMMARY *
2 MISST&E PROCESS DESCRIPTION *
3 SUMMARY RESULTS *
4 CONCLUSION *
APPENDIX A Letter Agreement *
APPENDIX B Terms Of Reference / SRTM *
APPENDIX C RFA Draft Final Report *
APPENDIX D RFE/RL Final Report *
APPENDIX E SAMPLE Penetration Test Plan Document *
TABLES OF:
FIGURES
Figure 1 Distribution of SRTM Criteria *
Figure 2 Ratification Of MISST&E Process *
TABLES
Table 1 SRTM Numeric Data Summary *
Table 2 Results of the MISST&E *
In September 2002, Radio Free Asia (RFA) and Radio Free Europe / Radio Liberty (RFE/RL) agreed to participate in a Mutual Information System Security Test and Evaluation (MISST&E) process. The MISST&E involved penetration testing by information security personnel within RFE and RFE/RL. This document, which includes recommendations, outcomes and appendices, is the final report on this activity.
The MISST&E process was proposed and accepted as methodology to determine system risks and vulnerabilities with the additional goals of:
These additional benefits did not constrain the most important short-term goal, which remained the assessment of threats and vulnerabilities as risks.
The positive effect of presentation of this MISST&E testing process was the development of heightened security awareness. In development of the Agreement between the agencies, the respective staff and CIO immediately became aware of obvious needs for improvement in information security function.
Although a modicum of testing was conducted by the agencies, this testing was too elementary and superficial to and an assessment of vulnerabilities and threats cannot be the basis of analysis in a requirements driven context. There are several possible factors to be considered that may have contributed to this outcome:
The assessment team recommends that follow-up MISST&E penetration testing program be developed to complete vulnerability determinations, and with these additional terms, conditions, and mutually acceptable requirements:
The origin of the MISST&E process is based upon a proposed method first described in an article, Media Convergence Info Warfare, in the trade journal Radio World (November 2000 page 19). This article germinated discussion with David Baden and expanded into subsequent discussions at the National Association of Broadcasters Convention (NAB 2000), the Mutual Information System Security Test and Evaluation (MISST&E) methodology has thus been developed as broadcast industry based method of penetration testing where the following goals are accomplished:
Organizations, within a related field or business purpose, test each other’s data systems for security weaknesses.
RFA and RFE/RL have similar goals, objectives and security concerns. In establishing two teams from commonly structured organizations, each team is composed of information security personnel possessing similar backgrounds, experience and training. The objective of this goal is not to produce a group of random ‘hackers’; rather, to enhance the understanding of personnel in each organization relating to types, methods and possible consequences of future attacks upon their own respective systems. With this knowledge, intruder response becomes more relevant and more timely to actual or attempted attacks, thereby optimizing defensive control
Network Security and Administrative personnel in each case gain valuable experience in what tools and techniques are available to breach the prevailing Security Architecture.
Tools and techniques used to attack RFA and RFE/RL are expected to be similar because the results sought by an intruder will be similar. The valuable experience to be gained by information security personnel is the hands-on knowledge of the methodologies to be reasonably expected in the future from the perspective of both aggressor and defender.
Each organization in preparation, testing and reviews, strengthens the defensive posture of their Networked Automated Information Systems.
The acts of preparation, testing and analysis of results develop a deeper appreciation of potential vulnerabilities by information security personnel in both RFA and RFE/RL. The objective of this goal is to establish the necessary nexus between penetration events and the security guidelines of the attached SRTM, and the interrelation between them in creating the most secure information protection of confidentiality, integrity and availability.
The Assessment Team developed a Security Requirements Traceability Matrix (SRTM) against which the testing was constrained. This matrix includes all relevant federal laws, regulations and guidelines, which either mandate, direct or recommend information assurance policies and procedures to protect the confidentiality, integrity and availability of information technology (IT) resources within a federal agency system. The SRTM has been scored as completely as possible using data from observation and team experience, as well a data from the limited testing conducted by the agencies. The Scoring system is comprised of the following four categories:
The SRTM used in the risk assessment phase of this project is separated into two distinct tabular formats: Security Requirements and Security Considerations:
Requirements that are beyond the scope of this assessment, not applicable to the project, or undetermined through limited testing may be rated as N/A or UNK, with an explanation placed in the Comments and Observations column. Items that remain untested after the completion of the test period are rated Not Tested (NT) without further comment.
The Two Charts Below Summarize the SRTM results:
|
|
|
|
Note: Based upon the Visual Comparison of the SRTM results, there is no comparative difference in security posture between RFA and RFE/RL. |
|
|
Source SRTM Appendix A |
|
Figure 1 Distribution of SRTM Criteria
The Charts below quantitatively summarizes the SRTM based test data:
|
Requirements Summary |
||
|
Subject |
RFA |
RFE/RL |
|
Met |
116 |
112 |
|
Not Met |
9 |
10 |
|
Partially Met |
17 |
18 |
|
Not Applicable |
37 |
37 |
|
Not Tested |
184 |
186 |
|
TOTAL Requirements |
363 |
363 |
Table 1 SRTM Numeric Data Summary
Our initial conclusion based upon this data is that due to the large number of Non Tested (NT) requirements is to discount a numerical scoring method as inconclusive. Future testing should not be prejudiced by this result, rather re-evaluation of the requirements and scoring are a reasonable remedial action.
The positive results of this exercise are detailed in the Table below:
Table 2 Results of the MISST&E
|
Positive Result |
RFE/RL |
RFA |
Comment |
|
Was Prime Directive Followed? |
No Negative Side Effects of testing to broadcast operations |
No Negative Side Effects of testing to broadcast operations |
No operational errors or deficiencies were reported by either side during the test period. |
|
Off site attacks of external ISP maintained Web sites |
No miss targeting reported. Internal web sites probed |
No miss targeting reported. Probed Internal web sites |
Both organizations maintain web sites controlled by external ISPs and internal sites. |
|
Benefits of Preparation for Attach |
Installation of Security Monitoring Equipment |
Maintenance of Security Monitoring Equipment |
Monitoring system |
|
Created Staff Awareness of and for Information Assurance and Security |
Validation of switch design and MAC lockdown methodology |
Validation of in house monitoring operation, DMZ and Coyote LRP security method. |
|
|
Investigation of offensive tools |
TBA |
Tools exercised and studied during attack phase included: nmap, nessus, nbtscan, fragroute, brutus, nikto, vomit and queso |
|
|
FTP Vulnerability |
Discovered |
Discovered |
Acceptable Risk in both cases |
|
MISST&E Report Availability |
STATE Inspector General, and GISRA process can validate |
STATE Inspector General, and GISRA process can validate |
Report represents evaluation of security which appears to be within the IA doctrine |
In summary, the MISST&E Exercise was successful and of benefit to both organizations, although additional testing is appropriate for a complete risk and vulnerability assessment. Cost-effectiveness is evident in that two distinct systems can be assessed simultaneously with limited funding by either organization for outside information assurance testing personnel, and these expenditures are comparable with the assessment of a single information system.
Specifically, and incorporated in their final report, RFA recognizes the benefits of the MISST&E process, and acknowledges that additional testing with modifications, addressed above, would represent a valuable tool in their information assurance program.
RFA and RFE/RL were able to detect and comprehend the vulnerabilities inherent in their respective organization’s file transfer protocol (ftp). A review of each system determined that the risk attendant to the ftp was at acceptable level for certification and the operation/maintenance phase of the life cycle of each system.
The level of security for each organization was improved. RFA developed a greater appreciation for the function and security enhancement features of their Internet Threat Monitor (ITM) program, and RFE/RL purchased and installed an ITM system, which now is installed and operational.
Beyond the bilateral decision to install ThreatSmartSM Internet Threat Monitor (T-ITM) external IP monitoring, Both the RFA and RFE/RL teams reviewed, prepared and enhanced their defensive postures.
Due to the nature of this report system security details described herein shall be light on specifics. As the system architecture of both facilities is of a security nature and should not be disclosed to public sources. Should either party object to any disclosure contained in this section, such disclosure shall be excised prior to delivery and distribution.
That said, we should quickly review our general understanding of RFA and RFE/RL defensive security architecture.
Overall, note that both RFA an RFE/RL program transmission is maintained on a private network, operated by the International Broadcast Bureau (IBB) as per mission. This facility and the public destination web sites maintained on separate ISPs, were specifically excluded from the MISST&E process as part of the agreement (see APPENDIX A). Public origination access for both RFE and RFA staff is handled in a decentralized way bureau by bureau each with common security architectural features. Our exercise in both cases related to testing the Security Architecture at the central offices. RFA maintains a central bureau in Washington DC, which enjoys 9 Mbs of a Fractional T3, while RFE/RL maintains an aggregate capability of 15 Mbs in Prague Czech Republic.
Both RFE/RL and RFA bureau offices maintain bridgehead servers facilities located in a DMZ. These servers provide web, file transfer and mail to the bureau networks. External service facilities at the RFE/RL are based largely on Microsoft Products, but appear maintained well and currently patched, while the RFA DMZ facilities are Apache and Exim based with a similar level of excellent maintenance. The most remarkable contrast between these external facilities is the use of CISCO PIX firewalls at RFE/RL in contrast to the firewall at RFE. The Firewall in use at RFA is an open source software appliance which runs on commodity PC hardware, allows for extensive configuration, including sshd, dhcp, forward and reverse proxy, as well as many other features. This single floppy firewall, called Coyote Linux. Operates from a write protect the boot floppy and hacking this is considered most difficult. Many high end security firms are actively using this same single floppy firewall technique.
In the case of RFA, The inside network is a private, non routable switched fabric which makes extensive use of open source software in a most secure manner. While RFE/RL maintains a routable fabric with MAC validation for switch operation (and therefore network access). In both systems, authentication is multi-layered.
Detailed in Appendix B, the RFA Staff report developed and tested numerous offensive tools; nmap, nessus, nbtscan, fragroute, brutus, vikto, and vomit, are cited in their report. Knowledge of the sources and methods of external penetration devices is cited as valuable insight by the RFA test team. Funds constrained witnessing RFE/RL activities Outside the Continental United States (OCONUS), however expect that similar results shall be reported from the European team. A visit to the Washington DC offices of RFE/RL revealed both offensive and defensive preparations.
Through the use of the MISST&E we have been able to determine that external penetration of two of the American Government's premier Surrogate Broadcast organizations are not subject to casual attack or successful disruption of their activities through ordinary means. Can it be said that extraordinary concentration or extreme methods are vulnerability for either site? Only subsequent testing can determine an answer. The positive aspects of this test process as summarized in Table I speak to a good beginning but information security is cyclic in implementation. As new staff and threats arrive at both of these institutions, there will remain a need to train and drill them in the proper methods to maintain and enhance information security within their respective organizations and architectures. This first MISST&E has demonstrated a remarkable value in enhancing security and should be considered a success.
One of the primary objectives of the MISST&E process is education and training of all parties involved in the testing exercises. This Assessment Team also undergoes a learning process each time the MISST&E is engaged between organizations. Observations can be made concerning potential improvements to the process, both internal and external to the participating organizations.
Although MISST&E was not fully applied in this project, the project remains successful in that it met goals relating to increased security awareness, demonstrated necessity for additional security hardware and services, and initial understanding of penetration processes by the participating organizations, RFA and RFE/RL. The following considerations are recommended in future testing using this process:
APPENDIX A Letter Agreement and Photo
On 19 September the following enabling document was signed:

Figure 2 Ratification Of MISST&E Process

|
Present (Left to Right) |
19 September 2002. |
|
|
|
|
|
|
|
|
|
|
|
|
(Photo by P Flint) |
APPENDIX B Terms Of Reference / SRTM
LETTER AGREEMENT
This agreement is between the respective Chief Information Officers (CIOs) of Radio Free Asia and Radio Free Europe / Radio Liberty, expressly for the purpose of establishing a Mutual Information Security System Testing and Evaluation (MISST&E) capability. This MISST&E shall begin Friday, November the First (11/1/2002) at Midnight Greenwich Mean Time (GMT) and shall end at Midnight Wednesday, November Twenty Seventh (9/27/2002) two thousand two.
This agreement along with its attachments comprises the entire guideline for this testing and evaluation. Any modification or abrogation of this agreement shall take place upon mutual agreement of the parties undersigned below, documented by written codicil addition to this letter.
The goal of this mutual test and evaluation activity is to accomplish information assurance excellence for both agencies.
The objectives in developing this capability include:
The agreed to test constraints and methodologies are included in this agreement as three attachments:
A report of the activities of the MISST&E shall be provided to both parties of this testing upon completion of the test and evaluation.
Signed and agreed to on this twenty-third day of September, two thousand two.
DAVID BADEN KENNETH MOREHOUSE
Chief Information Officer Chief Information Officer
Radio Free Asia Radio Free Europe
________________________________ _________________________________
PRIME DIRECTIVE
Radio Free Asia and Radio Free Europe are organizations that subsist on professionally delivered programming and subsidiary services.
This test process explicitly excludes the disruption of program and supporting services of either party. This test and evaluation process will not disrupt the program and program support activities of either party in any way.
Test scenarios shall specifically exclude the following:
Testing shall be constrained to documented scenarios that evaluate the requirements as set forth in the attached Security Requirements Trace-ability Matrix (SRTM). The test methodology shall be considered as a two-part process:
With respect to the Prime Directive, when a denial of service scenario appears possible, the testers developing the scenario are actively encouraged to:
The following Security Requirements Trace-ability Matrix (STRM) has been developed from and is traceable to the following specific United Stated Government information security laws, rules, regulations, and other guidance as stated below:
Additionally, this and other reference material as documented below has been considered and may be cited within the STRM:
PUBLIC LAWS
The Computer Security Act declares that improving the security and privacy of sensitive information in Federal computer systems is in the public interest, and creates a means for establishing acceptable security practices for such systems. It assigns NIST responsibility for developing standards and guidelines to assure the cost-effective security and privacy of sensitive information in Federal computer systems. Key provisions include:
The Paperwork Reduction Act, as amended in 1995, is the principal information resources management (IRM) statute for the Federal government. It required OMB to establish government-wide IRM policies and to oversee and review agency implementation. It requires the use of Information Technology (IT) to improve service, program management, increase productivity, enhance quality of decision-making, and reduce fraud and waste. It requires agency development of 5-year plans and the appointment of a senior IRM official. The Act assigned OMB responsibility for improving efficiency through use of new technologies.
The Act directs OMB to develop guidance on information security and to oversee agency practices. It directs agencies to establish computer security programs, and tasks OMB to develop and oversee the implementation of policies, principles, standards and guidelines on security. The act further directs Federal Agencies to apply a risk management process for information collected or maintained. Each agency must implement and enforce applicable policies, procedures, standards and guidelines on privacy, confidentiality, security, disclosures and information sharing.
Consistent with the Computer Security Act of 1987, agencies must identify and afford security protections commensurate with risk and magnitude of harm resulting from loss, misuse, unauthorized access to or modification of information collected or maintained.
The Information Technology Management Reform Act (ITMRA) relieved GSA of responsibility for procurement of automated systems and charged OMB with providing guidance, policy and control of information technology procurement. The ITMRA also requires the appointment of a Chief Information Officer (CIO) and mandates use of business process reengineering and performance measures to ensure effective IT procurement and implementation. The ITMRA also reaffirmed OMB, NIST and agency responsibilities regarding information security
This act addresses protection of the confidentiality, integrity and availability of data and systems and revises the Computer Fraud and Abuse Act. Unauthorized use of a computer to obtain information that could be used to injure the United States is a felony offense, as is intentional damage to computer. Reckless damage to a computer is a felony if committed by unauthorized individuals; but a misdemeanor offense if the damage were negligent, and not reckless. For authorized personnel, reckless or negligent damage is a misdemeanor offense with understanding that there is a range of additional administrative sanctions that may also be applied.
This Act requires the Director of OMB to provide direction and oversight in the acquisition of information technologies that provide for electronic submission, maintenance or disclosure of information as a substitute for paper. This Act also directs the acceptance of electronic signatures by executive agencies.
The Security Act (GISRA) amends the Paperwork Reduction Act by enacting new subchapters on information security, and primarily addresses the program management and evaluation aspects of security. Issues addressed include Life Cycle, incident response, agency performance plans, annual agency program reviews, annual Inspector General security evaluations, and required reports to OMB. The OMB is also required to report annually to congress.
The objective of the Privacy Act of 1974 is to protect personal privacy from invasions by Federal agencies. This law allows individuals to specify what information about them may be held by government agencies and gives individuals the right to obtain information held on them. The Act establishes civil and criminal penalties for violations. The act requires agency implementation fo physical security practices, information management practices, and computer and network controls necessary to ensure individual privacy.
This Act provides for fines and imprisonment for individuals who intentionally access a computer without authorization or exceeds authorized access and, by such means, obtains information deemed to require protection against unauthorized disclosure. Criminal and civil sanctions also apply to any individual who accesses a federal interest computer without authorization and alters, damages or destroys information, prevents authorized use of the computer, or traffics any password or similar information.
EXECUTIVE ORDERS
The purpose of this Order is to develop a strategy for protecting and assuring the continued operation of critical infrastructure, including the continuity of government. It established the Infrastructure Protection Task Force (IPTF) within the Department of Justice and the President’s Commission on Critical Infrastructure Protection. The Order requires all agencies to cooperate with the Commission and the IPTF, provide assistance, information and advice, and share information about threats and warning of attacks and information about actual attacks to the extent permitted by law.
This Order requires agencies to improve IT acquisition and management by implementing the relevant provisions of the Paperwork Reduction Act (PRA) and the Information Technology Management Reform Act (ITMRA). Agencies are instructed to refocus IT planning to more directly support their strategic mission, implement budget linked capital planning and investment process. Agencies must establish clear accountability for IT management by appointing a Chief Information Officer (CIO). Under this Order, agencies must:
This Order is established to protect against disruption of the operation of the information systems for critical infrastructure. It established the President’s Critical Infrastructure Protection Board, which is charged with recommending policies and coordinating programs for protecting information systems for critical infrastructure.
OTHER NATIONAL POLICY
PDD-63 focuses specifically on protecting critical infrastructures from both physical and "cyber" attack from sources within or without the United States. The lead Federal agency for the Public Health Services Infrastructure Sector is the Department of Health and Human Services (DHHS). This directive established the Critical Infrastructure Assurance Office (CIAO).
OMB A-123 implements the Federal Managers’ Financial Integrity Act and provides guidance to Federal managers on improving accountability and effectiveness of programs and operations by establishing, assessing, correcting and reporting on management controls. This Circular requires a review of security controls for each system whenever significant changes are made to a system, but at least every three years.
This Memorandum requires that every Federal web site must include a privacy policy statement, even it the site does not collect any information that results in the collection of a Privacy Act record. This statement must tell site visitors how any information from their site visit is handled by the agency. Privacy policies for agencies may be diverse and may be designed to the information practices of each individual site.
The purpose of this Memorandum is to reaffirm that, consistent with OMB A-130, agencies must continually assess risk to their computer systems and maintain adequate security commensurate with that risk.
Appendix III of this Circular establishes policy for the security of Federal automated information resources and incorporates requirements of the Computer Security Act of 1987 (P.L. 100-235) as well as responsibilities assigned in applicable security directives. A minimum set of security controls is established including development of a security plan, screening and training of individual users, risk assessments, disaster and contingency plans, and review of security safeguards at least every three years. Appendix III also incorporates provisions for automated information security programs and management control systems established in OMB Circular A-123. Specific requirements of Circular A-130 include:
This Memorandum provides guidance to agencies on carrying out the provisions of GISRA and focuses only upon areas of GISRA that introduce new or modified requirements. The Act requires annual Inspector General (IG) evaluations, agency reporting to OMB of the IG evaluations, and the required OMB annual report to congress.
This Memorandum establishes guidance for implementation of OMB M-01-24, directing agencies to submit to OMB plans of action and milestones (POA&M), with quarterly updates thereafter, to address all weaknesses identified by program reviews and IG evaluations required by GISRA and other previous OMB guidance.
Additionally, the following guidelines and publications of the National Institute of Standards and Technology (NIST) were drawn upon, utilized and referenced in the development of the SAMHSA AISSP.
The NIST Handbook is referenced frequently in OMB A-130, Appendix III and provides a broad overview for development of a sound approach to security controls. The handbook illustrates the benefits of security controls, major techniques for each control and addresses important related considerations.
This document provides a baseline to be used to establish and review Information Technology (IT) security programs. The security principles are to be applied in the use, protection, and design of government information systems.
LOCAL RULES
Local rules and regulations as presented to the reporting agency shall also be considered as requirements for this testing and evaluation process.
Security Requirements Trace-ability Matrix
The following Security Requirements Trace-ability Matrix (STRM) shall be the basis for all test scenarios developed by both parties for the duration of the test period. The supplied matrix can be used to support activity reporting in the columns provided.
|
Rating Key: |
|||||
|
M=Met PM=Partially Met NM=Not Met NA=Not Applicable NT=Not Tested |
|||||
|
Reference |
Requirement |
RFA Rating |
RFE/RL Rating |
Comments and Observations |
|
|
Administrative |
|||||
|
GISRA 3531(B)(3) GISRA 3533(a)(2)(B) GISRA 3534(a)(1) |
All United States Government agencies entities shall organize, implement, and maintain an information systems security program that ensures adequate security of all Government agencies information. It applies to all Government agencies bureaus, programs, teams, organizations, contractors, consultants, appointees, employees of Government agencies funded councils, associations, State, local as well as other government bureaus, and committees that use, process, manage Government agency information or meet the requirements of Federal computer system (defined in the Computer Security Act of 1987) |
M |
M |
|
|
|
GISRA 3534(A)(3)(A) GISRA 3524(a)(5)(A) |
The office of Chief Information Officer (CIO) and the designated department SA shall assure the objectives of OMB CircularA-130 (Appendix III) are being met by establishing the minimum security requirements and guidelines to appropriately implement personnel security, physical security, industrial security, automated information system security, telecommunications security, operations security, and compliance. |
M |
M |
|
|
|
NIST SP 800-18 |
The CIO and departmental SA’S shall maintain inventories of sensitive applications and facilities (operational and under development) by name and brief description. |
M |
M |
|
|
|
375 DM 19. |
All existing Government agencies systems shall be in compliance with the Government agencies Information Technology Security Policy (ITSP) |
PM |
PM |
Needs to be Assessed |
|
|
Local Rule |
Requests for exceptions to Government agencies security requirements must include sufficient information to allow for a reasoned decision |
M |
M |
|
|
|
Local Rule |
Permanent exemptions from the requirement to clear residual data will be based on a risk analysis to determine what damage, if any, is caused by the potential disclosure of sensitive information to a user who does not have the same authorization to use some or all of the sensitive information on the IT system. |
NT |
NT |
|
|
|
Local Rule |
No exemption to object reuse is required for stand-alone IT systems when all users are authorized access to all sensitive information on the IT system |
M |
M |
|
|
|
Local Rule |
A completed risk analysis shall accompany all requests for exemptions on existing dial-up circuits accessing sensitive IT systems. Time schedules will be included indicating when access control protection will be implemented on the dial-up circuits. |
M |
M |
|
|
|
Local Rule |
A written exception to the Office of Information Resource Management (PIR) shall be submitted for all facilities that cannot meet the baseline physical security requirements. |
NA |
NA |
|
|
|
GISRA 3534(A)(3)(A) |
A full –time Government agencies Department CIO with appropriate authority and responsibility to manage the sensitive IT system security program for the Government agencies shall be designated. |
M |
M |
|
|
|
NIST SP 800-18 |
The Department CIO shall establish a formal memorandum of understanding (MOU) among external agencies’ accrediting authorities preceding telecommunication interconnections of accredited IT systems |
M |
M |
Documents And Agreement |
|
|
ITMRA Sec. 5125 OMB 90-08 Sec. 6.a. CSA Sec. 2.B.3. CSA Sec. 6 |
The Department CIO shall establish departmental information security programs to ensure compliance with the objectives of OMB Circular – 130 (Appendix III) and the Government agencies Information Technology Security Policy (ITSP)
|
NT |
NT |
|
|
|
OMB 90-08 App |
The departmental CIOs shall determine the sensitivity of their information |
M |
M |
|
|
|
GISRA 3533(a)(2)(A |
The departmental CIO will decide the minimum safeguards prescribed for an IT system or network |
M |
M |
|
|
|
375 DM 19.9.A (6) NIST SP 800-18 OMB A-130 App. III |
The departmental CIO will execute a statement that an IT system or network is accredited |
NM |
NM |
|
|
|
375 DM 19.8.I (7) 375 DM 19.9.A. (3) 375 DM 19.9.C (4) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 GISRA 3533(a)(2)(A) GISRA 3534(b)(2) OMB 90-08 App. A OMB A-130 A.3.b.4 |
The departmental CIO will ensure that risk analysis responsibilities are accomplished in accordance with requirements |
M |
M |
|
|
|
GISRA 3534(b)(3) OMB 90-08 App. A 375 DM 19.9.A (4) OMB A-130 A.3.b.3 NIST SP 800-18 FISCAM SP 5.1 |
Management control systems must be established to document the requirements for each major information system and allow for periodic review of those requirements over the system’s life cycle. |
M |
M |
|
|
|
375 DM 19.9.A (7)&(5) GISRA 3533(b)(3) FISCAM AC-1.1 FISCAM AC-1.2 NIST SP 800-18 |
Management control processes shall be established to assure that appropriate administrative, physical, and technical safeguards are incorporated into new applications, and into significant modifications to existing applications |
M |
M |
|
|
|
FISCAM CC-2.1 NIST SP 800-18 |
The management control process for applications considered sensitive shall include security specifications, design reviews and system tests. |
M |
M |
|
|
|
FISCAM CC-2.1 NIST SP 800-18 GISRA 3534 (A)(2(C) GISRA 3534 (b)(3) |
Procedures shall be established for periodically reviewing the acquiring and operating information technology |
M |
M |
|
|
|
OMB A-130 A.3.b.2 NIST SP 800-18
|
Multi-year strategic planning processes shall be established for acquiring and operating information technology |
NM |
NM |
Suggested as a Recommendation |
|
|
OMB A-130 A.3.b.2 |
Responsibility for the security of each installation operated by or on behalf of the Federal Government shall be assigned to a management official knowledgeable in information technology and security matters. |
M |
M |
|
|
|
OMB A-130 A.3.b.1 FISCAM AC-2.1 |
The official whose program an information system supports shall be responsible and accountable for the products of that system. |
M |
M |
|
|
|
GISRA 3533(b)(3) GISRA 3534(A)(3)(A) GISRA 3524(a)(5)(A) GISRA 3534 (b)(2)(A) OMB 90-08 App A. |
An IT security program shall be implemented and maintained |
M |
M |
|
|
|
NIST SP 800-18 |
A level of security shall be established for all agency information systems commensurate with the sensitivity of the information and the risk and magnitude of loss or harm that could result from improper operation of the information system |
M |
M |
|
|
|
NIST SP 800-18 |
All IT system facilities shall ensure that legal agreements with vendors include provisions for security (security clearances, where necessary, conflict if interest agreements, bonding of employees, nondisclosure agreements personnel security screening, agreements establishing liability.) |
M |
M |
|
|
|
ITMRA Sec. 5125 OMB 90-08 App. A OMB-130 A.3.b.1 |
A Management Control Plan, which identifies: component inventory risk ratings (high, medium, low) material weaknesses, and other areas of management concern must be developed and updated annually. |
NT |
NT |
|
|
|
GISRA 3531 (B)(3) GISRA 3532 (b)(2) |
Each IT system or network being developed for operation beyond the year 2001 must be designed to meet the appropriate level of trust at which it is to be accredited. |
M |
M |
|
|
|
NIST SP 80-18 |
Departmental Security Analysis’s are required to thoroughly review all vendor recommendations and requirements for the configuration of security controls and formally document compliance or non-compliance of such requirements |
M |
M |
|
|
|
OMB 90-08 App A. 375 DM 19.7.A. 375 DM 19.9.B (2) FISCAM SP-1 FISCAM AC-1.1 FISCAM AC-1.2 NIST SP 800-18 FISCAM SD 1.2 |
Sensitive information shall be protected at a level commensurate with the threat. The level of protection will be determined by the criticality and sensitivity of the information and the mission supported by the system and in compliance with national policy and standards |
M |
M |
|
|
|
FIPS 140-2 FISCAM AC-3.2 |
Telecommunications and information systems transmitting sensitive information should incorporate approved protection techniques consistent with applicable ITSP policies in the most cost-effective manner. |
M |
M |
|
|
|
FIPS 140-2 |
The minimum systems security standards for telecommunications and computer systems which process, store, transfer, or communicate sensitive information with an identified threat other than foreign. E.g., criminal, shall be in compliance with the Federal Information Processing Standards (FIPS) |
M |
M |
|
|
|
375 DM 19.10 |
An annual internal control report shall be provided to the President and Congress that shall describe any security or other control weaknesses identified and provide assurance that there is adequate security of IT systems. |
NT |
NT |
|
|
|
GISRA 3534(b)(2)(A) GISRA 3534 (b)(2)(B) OMB 90-08 App. A 375 DM 19.8 I (7) 375 DM 19.9 A (3) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 |
A program should be established to conduct periodic risk analyses on IT systems to determine if security baselines are met and to ensure that appropriate, cost effective safeguards are incorporated on all new and existing IT systems and facilities. |
PM |
PM |
|
|
|
GISRA 3534(b)(2)(A) GISRA 3534 (b)(2)(B) OMB 90-08 App. A 375 DM 19.8 I (7) 375 DM 19.9 A (3) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 |
Threat assessments shall be conducted at least every three years to ensure appropriate protection is implemented on critical and sensitive Government agencies IT systems |
M |
NT |
First time testing RFE/RL |
|
|
GISRA 3534(b)(2)(A) GISRA 3534 (b)(2)(B) OMB 90-08 App. A 375 DM 19.8 I (7) 375 DM 19.9 A (3) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 |
A risk analysis shall be performed prior to the approval of design specifications for new installations |
NT |
NT |
|
|
|
GISRA 3534(b)(2)(A) GISRA 3534 (b)(2)(B) OMB 90-08 App. A 375 DM 19.8 I (7) 375 DM 19.9 A (3) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 |
A risk analysis must be performed to determine the need and type of approved protection techniques for critical or sensitive systems |
NT |
NT |
|
|
|
GISRA 3534(b)(2)(A) GISRA 3534 (b)(2)(B) OMB 90-08 App. A 375 DM 19.8 I (7) 375 DM 19.9 A (3) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 |
A risk analysis must be performed at periodic intervals established by the agency commensurate with the sensitivity of the data processed, but not to exceed every three years if no risk analysis has been performed during that period. |
NA |
NA |
|
|
|
GISRA 3534(b)(2)(A) GISRA 3534 (b)(2)(B) OMB 90-08 App. A 375 DM 19.8 I (7) 375 DM 19.9 A (3) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 |
A risk analysis shall be performed whenever there is significant change to the installation. A significant modification made to sensitive or critical IT system or network requires a review to determine the impact on the security of the processed sensitive information |
NM |
NM |
Configuration Management concerns. |
|
|
GISRA 3534(b)(2)(A) GISRA 3534 (b)(2)(B) OMB 90-08 App. A 375 DM 19.8 I (7) 375 DM 19.9 A (3) FISCAM SP-1 NIST SP 800-30 NIST SP 800-18 |
A risk analysis shall be performed for all critical IT systems or IT systems processing sensitive information |
NA |
NA |
|
|
|
Same As Above |
Risk assessments of Government agency’s telecommunications switch facilities shall be conducted to determine the types of threat and the appropriate physical protection measures. |
NT |
NT |
Critical to test |
|
|
375 DM 19.7.E NIST SP 800-18 OMB 90-08 App A |
Upon completion of system tests, a Certifying Official (Departmental CIO, and SAs) shall certify that the system meets all applicable Federal policies, regulations, and standards, and that the results of the tests demonstrate that the installed security safeguards are adequate for the application |
PM |
PM |
|
|
|
375 DM 19.9.A (4) 375 DM 19.9.A (7) 375 DM 19.9.B (4) NIST SP 800-18 FISCAM SP-1 FISCAM SP-5.1 |
All new or major upgrades of existing critical, sensitive, or foreign intelligence IT systems shall be formally certified through a comprehensive evaluation of the technical and non-technical security features |
PM |
PM |
|
|
|
OMB 90-08 App A 375 DM 19.7.E 375 DM 19.9.A (6) NIST SP 800-18 |
The certification, made as part of and in support of the accreditation process, shall determine the extent to which a particular design and implementation meets a specified set of security requirements. |
PM |
PM
|
||
|
Same As Above |
An official written declaration by an agency SA shall be issued for all certified IT systems and networks to operate with specified security safeguards. |
NT |
NT
|
|
|
|
375 DM 19.9.A (6) OMB A-130 A.3.b.4 NIST SP 800-18. |
Government agencies information systems that process critical, sensitive or foreign intelligence information will be certified and accredited by officially designated Agency CIO |
NA |
NA |
|
|
|
NIST SP 80-18 |
Security testing shall be accomplished for certification purposes after installation of a product. |
NT |
NT |
|
|
|
OMB 90-08 App A NIST SP 800-18 |
Pending accreditation, an interim approval to operate is permitted only if a security survey has been completed; a security plan has been developed to prevent unauthorized disclosure of data; a schedule describing advancement to the final accreditation must be established; and for systems processing TOP SECRET and foreign intelligence information, appropriate components must be located in properly secured facilities. |
NA |
NA |
|
|
|
NIST SP 800-18 |
Interim approval to operate must be employed when a new IT system is in an advanced test phase and must use some actual operational data for final design and test before initial operational capability. |
NA |
NA |
Cots Systems? |
|
|
NIST SP 800-18 |
Evaluation of the technical and non-technical security features of the IT systems and other safeguards shall be performed in support of the accreditation process. |
M |
M |
|
|
|
OMB 90-08 App A FISCAM CC-2.1 |
Appropriate technical, administrative, physical, and personnel security requirements must be included in specifications for the acquisition or operation of information technology installations, equipment, software, and related services and shall be reviewed and approved by the departmental ITSM or ADP Facility SM. |
NT |
NT |
Beyond the scope of this Assessment. |
|
|
NIST SP 800-18 FISCAM AC-1.1 FISCAM AC-1.2 |
Departmental SAs shall ensure that all new information systems that store, process, or communicate sensitive information have security features incorporated during the conceptual design phase. |
NT |
NT |
|
|
|
FISCAM AC-1.1 FISCAM AC-1.2 FISCAM CC-2.1 NIST SP 800-18 375 DM 19.8 B (8) 375 DM 19.9 A (7) |
Departmental IT SAs shall ensure that all new IT systems that are intended to process, store, or communicate sensitive information incorporate the provisions of Government agencies IT Security Policy during conceptual design phase |
NT |
NT |
|
|
|
FISCAM AC-1.1 FISCAM AC-1.2 FISCAM CC-2.1 NIST SP 800-18 375 DM 19.8 B (8) 375 DM 19.9 A (7) |
All new IT systems that store, process, transfer or communicate critical, sensitive or foreign intelligence information shall have systems security features incorporated during the conceptual design phase. |
NT |
NT |
|
|
|
FISCAM AC-1.1 FISCAM AC-1.2 FISCAM CC-2.1 NIST SP 800-18 375 DM 19.8 B (8) 375 DM 19.9 A (7) GISRA 3534(b)(3) 375 DM 19.9.A (4) OMB A-130 A.3.b.4 FISCAM SP-2.1 FISCAM SP 5.1 NIST SP 800-18 |
All new IT systems, which communicate critical or sensitive information, shall incorporate approved protection techniques during the planning stages and identify requirements the five-year information system plans. The Departmental SA shall periodically review all Government agencies information technology systems under their controls to ensure that provisions of the Government agencies IT SP are accomplished and provide a consolidated report to the DAA. |
NT |
NT |
||
|
FISCAM AC-1.1 FISCAM AC-1.2 FISCAM CC-2.1 NIST SP 800-18 375 DM 19.8 B (8) 375 DM 19.9 A (7) |
The designated system owner or departmental SA shall define and approve security requirements and specifications prior to acquiring or starting formal development of an IT system |
M |
M |
This document is the Security Requirements Traceability Matrix (SRTM) |
|
|
NIST SP 800-18 FISCAM CC-2.1 |
Design reviews and system tests shall be conducted and approved prior to placing the sensitive or critical application into operation. |
NT |
NT |
|
|
|
OMB 90-08 App A NIST SP 800-18 375 DM 19.9. B (9) |
Results of design reviews and system tests for sensitive or critical IT systems shall be fully documented and maintained in the official agency records. |
M |
NT |
|
|
|
NIST SP 800-18 FISCAM CC-2.1 |
Acquisition specialists shall conduct and approve system design reviews for critical or sensitive It systems prior to placing the system into operation to ensure the proposed design meets the approved security specifications. |
NA |
NA |
|
|
|
OMB 90-08 App A 375 DM 19.9.B (6) 375 DM 19.7.F NIST SP 800-18 OMB A-130 A.3.b.2.d FISCAM SC-3.1 FISCAM SC-2.3 FISCAM SC-2.1 |
Policies must be established and responsibilities assigned to assure that appropriate contingency plans are developed and maintained by the end users of sensitive and critical IT systems |
NM |
NM |
|
|
|
OMB 90-08 App A 375 DM 19.9.B (6) 375 DM 19.7.F NIST SP 800-18 OMB A-130 A.3.b.2.d FISCAM SC-3.1 FISCAM SC-2.3 FISCAM SC-2.1 |
Disaster recovery and continuity of operation plans for all Government agencies information technology installations that process critical or sensitive information shall be maintained |
PM |
M |
||
|
OMB 90-08 App A 375 DM 19.9.B (6) 375 DM 19.7.F NIST SP 800-18 OMB A-130 A.3.b.2.d FISCAM SC-3.1 FISCAM SC-2.3 FISCAM SC-2.1 |
Essential emergency functions shall be performed at the headquarters and regional levels to maintain continuity of government during the national security emergencies. |
NA |
NA |
|
|
|
NIST SP 800-18 FISCAM SC-2.1 |
The emergency operation records at storage locations for which the Vital Records Officer is accountable will be periodically inspected and certified for the currency and adequacy of the inventory following each inspection. |
NA |
NA |
|
|
|
FISCAM AC-3.1 FISCAM AC-4 FISCAM AC-4.1 FISCAM SC-2.1 NIST SP 800-18 |
Assembling, packing and arranging for shipment of the vital records to appropriate storage locations shall be assured. |
NA |
NA |
|
|
|
OMB 90-08 App A 375 DM 19.9.B (6) 375 DM 19.7.F NIST SP 800-18 OMB A-130 A.3.b.2.d FISCAM SC-3.1 FISCAM SC-2.3 FISCAM SC-2.1 |
OMB Circular A-130 requires appropriate contingency, disaster, and continuity planning for the IT systems applications and their implementation (facilities). The plan shall be tested periodically for their adequacy and effectiveness. |
NT |
NT |
Disaster Plans should be tested. |
|
|
OMB 90-08 App A 375 DM 19.9.B (6) 375 DM 19.7.F NIST SP 800-18 OMB A-130 A.3.b.2.d FISCAM SC-3.1 FISCAM SC-2.3 FISCAM SC-2.1 |
A disaster recovery and contingency plans shall be developed for IT systems processing sensitive or critical information. |
M |
NT |
|
|
|
375 DM 19.9.B (10) GISRA 3534(b)(2)(C) OMB 90-08 App A CSA Sec. 2.b.4 CSA Sec. 5 |
A security awareness and training program shall be established. |
PM |
PM |
|
|
|
GISRA 3534 (A)(3)(A) GISRA 3534 (b)(2)(C) OMB 90-08, App. A CSA 2.b.4. Sect. 5 OMB A-130 A.3.a.2.B 375 DM 19.7.F 375 DM 19.8.J (5) 375 DM 19.9.B (10) FISCAM SP-4.2
|
Training and awareness plans shall be developed, maintained, and updated annually by Government agencies bureaus. Plans must contain, at a minimum, the following information: (a) training content or subject matter: (b) target audience, including bureau and contractor personnel for each of the training content areas: and (c) level of training to be provided for each specific subject matter area and target audience category |
M |
M |
This |
|
|
Same As Above |
Government agencies personnel, including contractors, who are involved with the management, use or operation of any IT system handling sensitive or critical information within or under the supervision of the Department, shall receive periodic training in security awareness and accepted security practices |
PM |
PM |
|
|
|
Same As Above |
All personnel shall receive an annual threat briefing. |
NT |
NT |
|
|
|
GISRA 3533 (a)(2)(C) GISRA 3533 (a)(2)(C) NIST SP 800-18 |
Current IT system threat and vulnerability briefings shall be provided to Government agencies bureaus and business offices. |
NT |
NT |
|
|
|
GISRA 3534 (A)(3)(A) GISRA 3534 (b)(2)(C) OMB 90-08, App. A CSA 2.b.4. Sect. 5 OMB A-130 A.3.a.2.B 375 DM 19.7.F 375 DM 19.8.J (5) 375 DM 19.9.B (10) FISCAM SP-4.2 |
For users of IT systems which process, store or communicate critical or sensitive information, initial training shall be provided as soon as possible and within a minimum of 60 days of appointment for new personnel who are managers, users, or operators of sensitive information systems. |
NT |
NT |
|
|
|
Same As Above. |
For users of IT systems which process, store or communicate critical or sensitive information, continuing training shall be provided whenever there is significant change in the It system environment or procedures |
NT |
NT |
|
|
|
Same As Above. |
For users of IT systems which process, store or communicate critical or sensitive information, refresher training shall be provided on an annual basis for all personnel responsible for the management, use or operation of the IT system. |
NT |
NT |
|
|
|
Same As Above. |
All personnel who install, operate, maintain, or use critical or sensitive IT systems, shall be familiar with documented security practices before gaining access to the It system, and be acknowledged in writing applicable system security requirements and responsibilities. |
NT |
NT |
|
|
|
Privacy Act 522A(e)(10) |
Appropriate administrative, technical, and physical safeguards shall be established to ensure the security and confidentiality of records containing Privacy Act Information. |
NT |
NT |
|
|
|
Privacy Act 522A(e)(4)(E) |
Policies and practices regarding the storage, retrievability, access controls, retention, and disposal of Privacy Act Information shall be established. |
NT |
NT |
|
|
|
Same As Above |
Each agency that maintains a system of records shall promulgate rules, which establish procedures for the disclosure to an individual upon his request of his record. |
NT |
NT |
|
|
|
Privacy Act 522A(d)(1) (d)(2) (d)(3) (d)(4) |
Individuals shall be provided with access to, and the ability to amend errors in, systems of records consistent with the Privacy Act, Section 552 a.d. |
NT |
NT |
|
|
|
Privacy Act 522A(e)(5) |
Data shall be recorded and reported to provide users of the data with complete information about the subject of the report per OMB, Government agencies, and Privacy Act Standards. |
NT |
NT |
|
|
|
|
A five-year plan for a single integrated, efficient agency financial management system shall be developed. |
NT |
NT |
|
|
|
Local Rule |
Financial management data (for financial management systems) shall be gathered and processed only where necessary to meet specific internal management needs or external requirements. |
NT |
NT |
|
|
|
Local Rule |
Financial management data (for financial management systems) shall be recorded as soon as practicable after the occurrence of the event. |
NT |
NT |
|
|
|
Local Rule |
Financial management data (for financial management systems) shall be recorded and reported in the same manner throughout the agency, using uniform definitions. |
NT |
NT |
|
|
|
OMB A-130 A.3.a.2.f. GISRA 3534 (b)(2)(f) |
Financial management systems shall be designed and operated with reasonable total costs and transaction costs, in accordance with OMB guidelines. |
NT |
NT |
|
|
|
GISRA 3531 (B)(3) GISRA 3534 (a)(1) CSA Sec. 2.B.3. CSA Sec. 6. |
A plan for the security and privacy of each Federal computer system identified by that agency shall be established that is commensurate with the risk and magnitude or the harm resulting from the loss, misuse, or unauthorized access to or modification of the information contained in such system. |
NM |
NM |
FTP |
|
|
GISRA 3534 (b)(3) |
Security plans shall be reviewed annually. |
NT |
NT |
|
|
|
Local Rule |
The departmental Information Resource Management Officer shall appoint in writing a SA for IT systems under their control. |
NT |
NT |
Not authorized for |
|
|
Local Rule |
A memorandum with the appointed SA name, work address, telephone number, and security clearance (if applicable)_ shall be developed. |
NT |
NT |
|
|
|
GISRA 3534 (b)(2)(F) OMB A-130 A.3.a.2.d. FISCAM SP-3.4 NIST SP 800-18 |
The bureau IRM Coordinators will document the duties required to secure the IT system facility and the Bureau facility IRM will acknowledge these duties. |
NT |
NT |
|
|
|
CSA Sec. 2B.3. & Sec.6 GISRA 3534 (a)(1) GISRA 3534 (A)(3)(A) OMB 90-08 Sec. 6.a. OMB 90-08 App. A |
All Government agencies bureaus shall establish a network security program ensuring all IT systems and their supporting telecommunications are authorized, authenticated, protected, and accounted. |
PM |
PM |
|
|
|
NIST SP 80-18 |
All bureaus shall implement a program designed to minimize the risk of introducing viruses and other malicious software into Government agencies IT systems. |
M |
M |
|
|
|
NIST SP 80-18 |
PC systems to which access is somewhat open (i.e., training rooms, etc.) should never be used as a source of software or files to be transmitted and/or copied for distribution without first taking steps to ensure that the system is free from viruses or other malicious software. |
M |
M |
|
|
|
NIST SP 80-18 |
A virus or other malicious software program shall be immediately reported to agency supervisory personnel and the departmental ITTSM prior to being fixed. |
NT |
NT |
|
|
|
OMB A-130 A.3.b.2.a. NIST SP 80-18 |
An individual at any level of employment, who is determined to have been responsible for the unauthorized release or disclosure, or potential release or disclosure, of classified information, knowingly, willfully, or through negligence, shall be notified that the action is in violation of applicable Government agencies ITSP. |
NT |
NT |
|
|
|
OMB A-130 A.3.b.2.a. NIST SP 800-18 |
Any security violation possibly involving an infraction of Federal criminal laws shall be forwarded by the designated department ISSPM and concurrently to the Inspector General. |
NT |
NT |
|
|
|
Local Rule |
Government agencies bureaus shall submit annual "Agency Information Security Program Status" reports. |
M |
M |
|
|
|
FISCAM SS-3.1 NIST SP 800-18 |
The Office of Managing Risk and Public Safety shall maintain a record for not less than 12 months of all personnel requiring escorted access to computer equipment rooms, telecommunication facilities, and remote terminal areas, which has the visitor’s name, organization, reason for the visit, date and time of arrival and departure, and the escort’s name and signature |
NA |
NA |
|
|
|
FISCAM AC-3.1 NIST 800-18 |
The Office of Managing Risk and Public Safety shall maintain a current access roster containing the name, organization, and access authorization of each individual requiring routine unescorted access to computer equipment rooms, telecommunications facilities, and remote terminal areas. |
NA |
NA |
|
|
|
PERSCOM |
|||||
|
NIST SP 800-18 OMB A-130A.3.b.2.c. |
Personnel security policies and procedures shall be established and managed to assure an adequate level of security for Federal IT systems |
NT |
NT |
||
|
NIST SP 800-18 |
The coding of position sensitivity is required on Optional Form 8, Position Description (or equivalent agency form). Bureaus must use the following codes when coding position sensitivity: Special Sensitive – 4, Critical Sensitive – 3, Non-critical Sensitive –2, No sensitive –1. The letter "C" will also identify computer and ADP positions after the above code. |
NT |
NT |
|
|
|
OMB A-130 A.3.b.2.c |
Position sensitivity criteria, similar to what is applied to Federal personnel, must be applied to contractor relationships. |
NT |
NT |
|
|
|
OMB A-130 A.3.b.2.c |
All positions that have national security duties must be designated at national security sensitivity levels. Levels include Special Sensitive, Critical Sensitive, and Non-Sensitive. |
NA |
NA |
|
|
|
Local Rule |
The individuals designated as representatives to the Government agencies Telecommunications and Information Systems Security Working Group should have or should be eligible for a SECRET clearance. |
NT |
NT |
|
|
|
OMB A-130 A.3.b.2.c |
Required background investigations are required for placement at each of the sensitivity levels: Special Sensitive: Special Background Investigation; Critical Sensitive: Background Investigation (BI); Non-critical Sensitive: Limited BI or Minimum BI; Non-sensitive: National Agency Check and Inquiry (NAC&I). |
NA |
NA |
|
|
|
OMB A-130 A.3.b.2.C. |
The incumbent of each position designated Special Sensitive or Critical Sensitive shall be subject to periodic reinvestigation five years after placement, and at least once each succeeding five years. |
NA |
NA |
|
|
|
OMB A-130 A.3.b.2.c |
Personnel applying for critical sensitive positions must undergo a pre-placement background investigation. |
NA |
NA |
|
|
|
OMB 90-08 App A |
Only authorized personnel shall have access to information systems. |
M |
M |
|
|
|
OMB 90-08 App A NIST SP 800-18 FISCAM AC-2 FISCAM AC-2.1 FISCAM AC-3.2 |
Granting access to any classification level must be made on a need-to-know basis, and when that need no longer exists, access must be canceled. |
M |
M |
||
|
GISRA 3534 (b)(2)(C) OMB 90-08 App A OMB A-130 A.3.a.2.b. |
On-site personnel who operate ADP equipment shall be approved for access to all types of restricted access data contained in the system and instructed on appropriate security procedures before being granted unescorted system access. |
M |
M |
|
|
|
OMB A-130 A.3.b.2.b. |
Appropriate supervisors and security professionals shall be approved for access to all types of restricted access data contained in the IT system and instructed on appropriate security procedures before being granted unescorted system access. |
M |
M |
|
|
|
OMB A-130 A.3.b.2.b |
Personnel who design, develop, install, modify, service, or maintain the operating system software shall be approved for access to all types of restricted-access data contained in the system and instructed on appropriate security procedures before being granted unescorted access. |
M |
M |
|
|
|
OMB A-130 A.3.b.2.b |
Communication specialists who are responsible for maintenance of the communications hardware and software among ADP facility and its remote terminal users and have the capacity to monitor unencrypted communications shall be approved for access to all types of restricted access data contained in the system and instructed on appropriate security procedures before being granted unescorted system access. |
NT |
NT |
|
|
|
Local Rule |
Bureaus shall provide written identification of the definition of any respective legend(s) and establish protective requirements, as applicable, which shall be made known to all authorized recipients. |
NT |
NT |
|
|
|
Local Rule |
The legend "Limited Official Use" (LOU), shall be marked, stamped, pr permanently affixed to the top and bottom of the outside of the front and back covers, on the title page, on the first and last pages and on all pages of documents or information. |
NA |
NA |
|
|
|
Local Rule |
The identity of the official authorizing the use of the legend and the date of such authorization shall appear on the first and last pages of all LOU documents or information. |
NA |
NA |
|
|
|
Local Rule |
Legends should be removed as soon as they are no longer needed. |
NA |
NA |
|
|
|
Local Rule |
The identity of the official authorizing the "de-control" of a document or information, as well as the date of such authorization, shall appear on the first and last pages of all decontrolled documents. |
NA |
NA |
|
|
|
Local Rule |
Cover sheets must be used to protect the LOU information while in use. |
NA |
NA |
|
|
|
Local Rule |
File folders containing LOU information shall be marked (e.g., at the top and bottom of the front and back covers). |
NA |
NA |
|
|
|
Local Rule |
A warning label shall be affixed to diskettes or floppy disks that contain LOU. |
NA |
NA |
|
|
|
Local Rule |
Officials authorized to control and /or decontrol LOU information shall be listed by name and position title. |
NA |
NA |
|
|
|
Local Rule |
Government agencies officials responsible for responding to the request for release of LOU shall determine, under FOIA/Privacy Act criteria or the appropriate regulations of the Government agencies agency concerned, whether the information should be made available to the requestor. |
NA |
NA |
|
|
|
Local Rule |
Security Standards equivalent to national security CONFIDENTIAL are required for information marked for LOU when the information is electronically processed, stored, transferred, or communicated. |
NA |
NA |
|
|
|
Local Rule |
Safeguard LOU information in the same manner as national security information classified CONFIDENTIAL. |
NT |
NT |
|
|
|
Local Rule |
LOU information shall be made available only to those persons having a need-to-know. |
NT |
NT |
|
|
|
Local Rule |
LOU information or material shall NOT be hand-carried aboard commercial passenger aircraft by employees or agency officials unless the security representatives authorized to direct official travel within their office or agency has made a prior written determination that an emergency situation exists. |
NT |
NT |
|
|
|
Local Rule |
LOU information or material shall normally be transmitted by one of the means established for higher classifications or by the U.S. Postal Service Express Mail or U.S. Postal Service registered first class mail. |
NT |
NT |
|
|
|
Local Rule |
Personnel designated as couriers shall have in their possession an employee ID card or credential with a photograph, description data and bearer’s signature. |
NT |
NT |
|
|
|
Local Rule |
Travelers shall NOT authorize the opening of carry-on items under any circumstance. |
NA |
NA |
Local Policy |
|
|
Local Rule |
LOU documents being carried shall be in the form of paper documents with no metal bindings and contained in sealed opaque inner and outer envelopes. |
NA |
NA |
|
|
|
Local Rule |
Officials who authorize transportation of classified and LOU information material shall notify an official of the appropriate air carrier in advance. |
NA |
NA |
|
|
|
Local Rule |
Couriers shall have an original of a letter authorizing them to carry classified or LOU information or material. |
NA |
NA |
|
|
|
Local Rule |
All pages of a LOU transmittal document shall show the control designation of the information being transmitted. |
NA |
NA |
|
|
|
|
The Department SM shall ensure the procedures are developed to protect sensitive reports during preparation, transmittal, receipt and storage. |
NT |
NT |
|
|
|
Local Rule |
Copies of risk analysis shall be available to risk analysis teams, internal control personnel and the agency ISSPM on a need-to-know basis. Reports shall be kept in a secure area commensurate with the sensitivity of information contained in the report. |
NT |
NT |
|
|
|
Local Rule |
A copy of all documentation relating to security violations shall be filed in the security violations indexes of the Government agencies Office of the Inspector General, or the department ISSPM, and also in the individual’s personnel security file. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Procedures will be in place to ensure the secure destruction of discarded computer material to preclude unauthorized disclosure. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Personally-owned computers or software will be not be used to process, access, or store sensitive information without the approval of the department Heads of Bureaus. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Configuration controls plans shall be prepared and configuration management shall be implemented in all critical, sensitive and foreign intelligence IT systems. |
M |
M |
|
|
|
NIST SP 800-18 |
Configuration control should begin in the earliest stages of the design and development of the IT systems and extend over the full life of the configuration items included in the design and development stages. |
M |
M |
|
|
|
OMB 90-08 App A NIST SP 800-18 FISCAM CC-2.1 FISCAM CC-3.1 FISCAM SS-3.2 |
For every change that is made to an IT system, the design and requirements of the changed version of the IT system should be identified. |
NA |
NA |
||
|
Same As Above |
Every change that is made to documentation, hardware, and software/firmware should be reviewed and approved by the department Heads of Bureaus, Network Security Officer, or the available security staff. |
NT |
NT |
|
|
|
Same As Above |
Configuration status accounting is responsible for recording and reporting on the configuration of the project throughout the change. |
NT |
NT |
|
|
|
Same As Above |
Through the process of a configuration audit, the completed change can be verified to be functionally correct, and for trusted systems and networks, consistent with the security policy of the system or network. |
NT |
NT |
|
|
|
Same As Above |
In the case of a change to hardware or software/firmware that will be used at multiple sites, configuration control is also responsible for ensuring that each site receives the appropriate version of the IT system. |
NT |
NT |
|
|
|
OMB 90-08 App A 375 DM 19.7.D. 375 DM 19.9.C (2) FISCAM AC-2 NIST SP 800-18 FISCAM AC-3.2 FISCAM AC-4 |
The IT system will assure that users without authorization are not allowed access to the data. |
M |
M |
|
|
|
Same As Above |
System owners shall be provided the capability to specify, at their discretion, who ) by individual user, groups, etc.,) may have access to their data. |
M |
M |
|
|
|
375 DM 19.9.C (1) NIST SP 800-18 |
The IT system shall require users to identify themselves and provide some proof that they are who they say they are (e.g., user ID and password). |
M |
M |
||
|
NIST SP 800-18 375 DM 19.8.N |
A password should not be shared by multiple users. |
PM |
PM |
FTP Site |
|
|
NIST SP 800-18 |
The IT should prevent a user from choosing a password that is already associated with another user ID. |
NT |
NT |
|
|
|
375 DM 19.9.C (2) |
The IT system should store passwords in a one-way encrypted form. |
M |
M |
|
|
|
FISCAM AC-3.2 NIST SP 800-18 OMB 90-08 App A |
The IT system should automatically suppress or fully blot out the clear-text representation of the password on the data entry device. |
M |
M |
|
|
|
FISCAM AC-3.2 NIST SP 800-18 OMB 90-08 App A |
The IT system should block any demonstration of password length (i.e., the cursor should not move upon input). |
NM |
NM |
||
|
NIST SP 800-18 FISCAM AC-2 FISCAM AC-3.2 |
The IT system, by default, should not allow null passwords during normal operation. |
M |
M |
|
|
|
375 DM 19.9.C (2) FISCAM AC-3.2 NIST SP 800-18 OMB 90-08 App A |
Passwords and user ID s should be immediately removed when an authorized user no longer needs access to the IT system. |
NT |
NM |
|
|
|
FISCAM AC-3.2 NIST SP 800-18 |
The IT system should provide a mechanism to allow passwords to be user-changeable. |
M |
M |
|
|
|
375 DM 19.9.C (1) FISCAM AC-3.2 NIST SP 800-18 OMB 90-08 App A |
The IT system should enforce password aging on a per-user basis. The system-supplied default for non-privileged users should be on more than 60 days and no more than 30 days for user ID s that may acquire privileges. After the password-aging threshold has been reached, the password shall no longer be valid and should require action by the department System Owners/Managers to reset the password. |
M |
M |
||
|
NIST SP 800-18 FISCAM AC-3.2 |
The system should provide a mechanism, which notifies the user to change their password. |
M |
M |
||
|
NIST SP 800-18 FISCAM AC-3.2 |
Passwords should not be reusable by the same individual for a period of time specified by the department IT USERS. The system-supplied default should be six months. |
M |
M |
||
|
NIST SP 80-18 OMB 90-08 App A |
The IT system should provide a method of ensuring the complexity of user-entered passwords (e.g., eight characters minimum length). |
M |
M |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
As soon as the It system has been installed, all vendor supplied passwords, including those for software packages and maintenance accounts should be changed. |
M |
M |
|
|
|
NIST SP 800-18 |
Terminals, workstations, and networked personal computers should never be left unattended when user ID and password have been logged in. |
M |
M |
|
|
|
NIST SP 800-18 |
IT systems which process, store, or transmit sensitive information shall meet the requirements for Controlled Access level protection as evaluated by the National Security Agency or the National Institute for Standards and Technology |
NA |
NA |
|
|
|
NIST SP 800-18
|
If a network is accessed by a user who is not authorized to use all or some of the sensitive information processed by or communicated over the network (or if the network is accessed by dial-up circuits), Controlled Access protection shall be implemented on microprocessors running UNIX or other multi-user, multi-tasking operating systems As an interim measure, specialized automated techniques shall be used to verify the proper output classification of data until the incorporation of trusted products is feasible, or a new IT system can be designed and implemented to meet the specified requirements When a storage object (e.g. core area, disk file, etc.) is initially assigned, allocated, or reallocated to a system user, the IT system shall assure that it has been cleared. |
M
M |
M
M
|
||
|
NIST SP 800-18 FISCAM AC-3.2 |
The IT system shall define and control access between named users and system resources (e.g. files and programs) |
M |
M |
|
|
|
GISRA 3531(B)(3) CSA Sec. 2.B.3 CSA Sec. 6. OMB 90-08 App A FISCAM AC-2.1 FISCAM AC-3.2 |
Sensitive IT systems shall be protected to at least the minimum level of Controlled Access protection. |
M |
M |
||
|
NIST SP 800-18 OMB 90-08 App A FISCAM AC-3.2 |
The IT system must protect authentication data so that it may not be accessed by an unauthorized user. |
M |
M |
||
|
OMB 90-08 App A NIST SP 800-18 FISCAM AC-4.3 |
The IT system shall be able to create, maintain, and protect from modification, unauthorized access or destruction of an audit trail of accesses to the resources it protects |
M |
M |
||
|
Same As Above |
The audit data shall be protected by the IT system so that read access to it is limited to those who are authorized for audit data. |
M |
M |
|
|
|
Same As Above |
The IT system shall be able to record the following types of events: log on, log off, change of password, creation, deletion, opening, and closing of files, program initiation, and all actions by system operators, administrators, and security officers. For each recorded event, the audit record shall identify: date and time of the event, user type of event and the success or failure of the event. |
M |
M |
|
|
|
Same As Above |
For log on, log off, and password change the origin of the request (e.g. terminal ID) shall be included in the audit record. For file related events, the audit record shall include the file’s name. |
M |
M |
|
|
|
NIST SP 800-18 |
The Departmental System Managers shall be able to selectively audit the actions of one or more users based on individual identity. |
M |
M |
|
|
|
OMB A-123 |
Audit procedures shall be developed and coordinated with other internal control procedures required under OMB Circular A-123 |
NT |
NT |
|
|
|
NIST SP 800-18 FISCAM SC-1.1 FISCAM SC-2.1 FISCAM SC 3.1 |
New software should be backed up immediately, retaining the original distribution diskettes in a safe and secure location. "Write-protect original diskettes prior to making up backup copies |
NT |
NT |
||
|
Same As Above |
Data files should be backed up frequently and stored off-site or in a secured environment. |
NT |
NT |
|
|
|
FISCAM SC-3.1 |
Damaged software programs should be restored from the original diskettes, not from regular backups. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Use only new media for making copies for distribution. |
NT |
NT |
|
|
|
NIST SP 800-18 |
PC machine-readable media should be scanned for malicious software before initial use. Write-protect software, prior to scanning to prevent possible contamination from system and virus scan software being used. |
M |
M |
|
|
|
NIST SP 800-18 |
Software obtained electronically from bulletin boards shall be downloaded to newly formatted diskettes and not directly to the computer hard disk. |
PM |
PM |
COMMENT |
|
|
Local Rule |
PC hard disk drives, network file servers and other media that will be used to handle agency information should be formatted between the time they are received and put into use. |
M |
M |
|
|
|
Local Rule |
Never start up (boot-up) a computer from a diskette unless it is the original write-protected system master or a trusted copy. |
M |
M |
|
|
|
NIST SP 800-18 |
Portable computer systems, such as laptops, that leave agency controlled areas shall be scanned for viruses before and after connecting to systems or software owned by other organizations. |
M |
M |
|
|
|
GISRA 3533(a)(2)(A) GISRA 3533 (a)(2)(B) GISRA 3534 (a)(1) |
The decision to safeguard sensitive storage media during its lifecycle should be based on a risk analysis to access the threat to the sensitive information. |
M |
M |
|
|
|
NIST SP 800-18 |
A purge is not complete until a final overwrite is made using unclassified data. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Media should be purged before submitting it for destruction. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Degaussing with an approved degausser is the only method acceptable for purging classified or unclassified intelligence information media. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Overwrite software shall be protected at the level of the media it purges. Overwrite software must be protected from unauthorized modification. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Magnetic tape should have a label applied to the reel that identifies the coercively of the media. Labels that show the classification should not be removed from the reel until he media is declassified. |
NA |
NA |
|
|
|
NIST SP 800-18 |
Leased equipment containing non-removable magnetic storage media should not be returned to the vendor unless the media is declassified using an approved procedure. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Once sensitive information has been written to the hard-drive of a personally owned computer, the sensitive data shall be completely erased when it is no longer needed on the IT system to preclude disclosure or data corruption. |
NT |
NT |
|
|
|
OMB 90-08 App A FISCAM CC-3.2 FISCAM CC-3.3 FISCAM SS-3.2 |
Controls for local area a networks shall be established that prevent anyone except authorized staff from loading software on file severs. |
M |
M |
||
|
NIST SP 800-18 |
A local area network file server shall never be used as a workstation. |
NA |
NA |
|
|
|
NIST SP 800-18 FISCAM AC-3 FISCAM AC-3.1 |
File servers shall be located in areas where access is restricted. |
M |
M |
||
|
|
Security Features User’s Guide: A single summary, chapter, or manual in user documentation shall describe the security features provided by the Trusted Computer Base, guidelines on their use and how they interact with one another. |
NM |
NM |
|
|
|
|
A Trusted Facilities Manual: A manual addressed to the ADP security administrator shall present cautions about functions and privileges that should be controlled when running a secure facility. |
NM |
NM |
|
|
|
OMB 90-08 App A OMB A-130 A.3.b.2.e. NIST SP 800-18 FISCAM CC-2.1 FISCAM SS-3.1 FISCAM SS-3.2 |
Test documentation: The system developer shall provide to the evaluators a document that describes the test plan, test procedures that show how the security mechanisms were tested, and the results of the security mechanisms’ functional testing. |
M |
M |
This document |
|
|
Same As Above |
Design documentation: Documentation shall be available that provides a description of the manufacturers philosophy of protection and an explanation of how this philosophy is translated into the Trusted Computer Base (TCB). If the TCB is composed of distinct modules, the interfaces between these modules shall be described. |
NM |
NM |
|
|
|
NIST SP 800-18 |
Written certification from the vendor that the demonstration software has been checked and is free from viruses shall be obtained prior to loading any vendor software. |
NT |
NT
|
|
|
|
|
RISK MANAGEMENT |
|
|
|
|
|
NIST SP 800-18 |
The current Information Assurance Proponent’s system configuration is documented, including links to other systems. |
PM |
M |
|
|
|
FISCAM SP-1 |
The Information Assurance Proponent performs and documents risk assessments on a periodic basis, or whenever the system, facilities, or other conditions change |
M |
PM |
|
|
|
FISCAM SP-1 |
Sensitivity and integrity of information is considered in the risk assessment process. |
M |
M |
|
|
|
FISCAM SP-1 |
Threat sources, both natural and manmade are identified in the risk assessment process. |
M |
M |
|
|
|
NIST SP 800-30 |
Known system vulnerabilities, flaws, or other weaknesses that could be exploited have been documented, updated and maintained. |
PM |
PM |
|
|
|
NIST SP 800-30 |
The Information Assurance Proponent risk assessment includes an analysis that determines whether security controls are in place to adequately mitigate vulnerabilities. |
PM |
PM |
|
|
|
FISCAM SP-1 |
The Information Assurance Proponent’s risk determinations and related management approvals are documented and maintained on file. |
M |
M |
|
|
|
NIST SP 800-30 |
The Information Assurance Proponent conducts an impact analysis as part of the risk assessment process. |
M |
M |
|
|
|
NIST SP 800-30 |
As part of the risk assessment process, the Information Assurance Proponent identifies, and seeks to implement additional controls sufficient to mitigate identified risks. |
M |
M |
|
|
|
|
|
|
|
|
|
|
|
SECURITY CONTROLS |
|
|
|
|
|
FISCAM SP-5.1 |
The Information Assurance Proponent system and network boundaries are subjected to periodic reviews. |
M |
M |
|
|
|
FISCAM SP-5.1 NIST SP 800-18 |
The Information Assurance Proponent conducts a review of security controls when a significant change occurs. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent conducts routine self-assessments of security controls. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent conducts routine tests and examinations of key security controls, including scans, analyses of settings and penetration testing. |
M |
M |
|
|
|
FISCAM SP-3 FISCAM SP-4 NIST SP 800-18 |
Security alerts and security incidents are analyzed and remedial actions are taken. |
M |
M |
|
|
|
FISCAM SP-5.1 FISCAM SP-5.2 NIST SP 800-18 |
The Information Assurance Proponent employs a timely and effective process for reporting significant weaknesses and ensuring effective remedial actions. |
M |
M |
|
|
|
|
LIFE CYCLE CONSIDERATIONS |
|
|
|
|
|
FISCAM AC-1.1 FISCAM AC-1.2 NIST SP 800-18 |
Sensitivity of the Information Assurance Proponent’s system is considered in the initiation phase of the life cycle. |
NT |
NT |
|
|
|
FISCAM AC-1.2 |
Authorizations for software modifications are documented and maintained. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Security requirements are identified during system design in the development/acquisition phase of the life cycle. |
NT |
NT |
|
|
|
NIST SP 800-18 |
An initial risk assessment is performed by the Information Assurance Proponent to determine security requirements in the development/acquisition phase of the life cycle. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Appropriate security controls with associated evaluation and test procedures are developed before the Information Assurance Proponent’s procurement action. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Solicitation documents include security requirements and test/evaluation procedures. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Requirements in the solicitation documents permit updating security controls as new threats/vulnerabilities are identified and new technologies are implemented. |
NT |
NT |
|
|
|
FISCAM CC-2.1 NIST SP 800-18 |
Design reviews and system tests are conducted prior to placing a system in production in the implementation phase of the life cycle |
NT |
NT |
||
|
FISCAM CC-2.1 NIST SP 800-18 |
Test results in the implementation phase of the life cycle are documented. |
NT |
NT |
||
|
NIST SP 800-18 |
Certification testing of security controls is conducted and documented in the implementation phase of the life cycle. |
PM |
PM |
||
|
NIST SP 800-18 |
System documentation is modified to reflect additions of security controls. |
NT |
NT |
|
|
|
FISCAM CC-2.1 NIST SP 800-18 |
Following the addition of security controls since development, the affected system is tested and recertified. |
NT |
NT |
|
|
|
NIST SP 800-18 |
In the implementation phase of the life cycle, the Information Assurance Proponent applications undergo a technical evaluation to ensure that they meet applicable federal laws, regulations, policies, guidelines and standards. |
NT |
NT |
||
|
NIST SP 800-18 |
In the implementation phase of the life cycle, the affected Information Assurance Proponent has written authorization, either full or interim. |
NT |
NT |
|
|
|
FISCAM SP-2.1 NIST SP 800-18 |
An Information Assurance Proponent system security plan has been developed and approved as part of the operation/maintenance phase of the life cycle.. |
M |
M |
|
|
|
NIST SP 800-18 |
Security controls have been developed and disseminated to owners of interconnected systems. |
NT |
NT |
||
|
FISCAM SP-2.1 NIST SP 800-18 |
The Information Assurance Proponent’s security plan is kept updated and maintained for best practices. |
NT
|
NT |
||
|
NIST SP 800-18 |
In the disposal phase, official electronic records are properly disposed/archived. |
NT |
NT |
|
|
|
FISCAM SP-3.4 NIST SP 800-18 |
Information or media is purged, overwritten, degaussed, or otherwise destroyed when disposed or used elsewhere. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent maintains records concerning disposal actions and verification of sanitization. |
NT |
NT |
|
|
|
|
AUTHORIZE PROCESSING (CERTIFICATION & ACCREDITATION) |
|
|
|
|
|
NIST SP 800-18 |
Technical and/or security evaluations are conducted when a significant change is implemented. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Risk assessments are conducted whenever significant changes are implemented. |
PM |
PM |
|
|
|
NIST SP 800-18 |
Rules of Behavior have been established and signed by users. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent has developed, implemented and tested a contingency plan |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent has developed, updated and reviewed a system security plan. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent security controls are implemented and operating as intended. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent security controls are consistent with the identified risks and the system and data sensitivity. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent management has authorized all interconnections. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent management initiates prompt action to correct deficiencies. |
NT |
NT |
|
|
|
|
SYSTEM SECURITY PLAN |
|
|
|
|
|
FISCAM SP-2.1 NIST SP 800-18 |
Key affected parties and management approve the Information Assurance Proponent’s system security plan. |
NT |
NT |
|
|
|
NIST SP 800-18 |
A summary of the Information Assurance Proponent system security plan is incorporated in the strategic IRM plan. |
NT |
NT |
||
|
FISCAM SP-2.1 NIST SP 800-18 |
The Information Assurance Proponent’s system security plan is reviewed periodically and adjusted to reflect current conditions and risks. |
NT |
NT |
|
|
|
|
OPERATIONAL CONTROLS |
|
|
|
|
|
FISCAM SD-1.2 NIST SP 800-18 |
All Information Assurance Proponent information technology positions are reviewed for sensitivity level. |
NT |
NT |
|
|
|
FISCAM SD-1.2 |
The Information Assurance Proponent maintains document job descriptions that accurately reflect assigned duties and responsibilities, and segregate duties. |
NT |
NT |
|
|
|
FISCAM SD-1 NIST SP 800-18 |
Sensitive functions are divided among different individuals. |
NT |
NT |
||
|
FISCAM SP-4.1 NIST SP 800-18 |
The Information Assurance Proponent implements a standard process for requesting, establishing, issuing and closing user accounts. |
NT |
NT |
||
|
FISCAM SP-4.1 |
Any Information Assurance Proponent personnel authorized to bypass significant technical and operational controls are screened prior to access and periodically thereafter. |
NT |
NT |
||
|
FISCAM SP-4.1 |
Confidentiality agreements are required of all Information Assurance Proponent personnel assigned to work with sensitive information. |
NT |
NT |
||
|
FISCAM AC-2.2 NIST SP 800-18 |
System access prior to screening requires appropriate written authorization. |
NT NT |
NT |
||
|
|
PRODUCTION, INPUT/OUTPUT CONTROLS |
|
|
|
|
|
NIST SP 800-18 |
Information Assurance Proponent maintains a help desk. |
M |
M |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent maintains processes to ensure unauthorized individuals cannot read, copy, alter, or steal printed or electronic information. |
M |
M |
|
|
|
NIST SP 800-18 |
Only authorized personnel may pick up, receive, or deliver input and output information and media. |
M |
M |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent utilizes audit trails for receipt of sensitive inputs/outputs. |
M |
M |
|
|
|
NIST SP 800-18 |
Controls are in place for transportation of media or printed output. |
M |
M |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent maintains audit trails for inventory management. |
M |
M |
|
|
|
FISCAM AC-3.4 NIST SP 800-18 |
System media is sanitized prior to reuse |
M |
M |
|
|
|
NIST SP 800-18 |
Damaged media is either stored appropriately or destroyed. |
M |
M |
|
|
|
NIST SP 800-18 |
Hardcopy media is shredded or destroyed when no longer needed. |
M |
M |
|
|
|
|
CONTINGENCY PLANNING |
|
|
|
|
|
FISCAM SC-1.1 FISCAM SC 3.1 NIST SP 800-18 |
The Information Assurance Proponent identifies critical files and operations and backups are conducted and documented. |
NT |
NT |
||
|
FISCAM SC-1.2 |
The Information Assurance Proponent has identified resources supporting critical operations. |
NT |
NT |
|
|
|
FISCAM SC-1.3 |
Processing priorities have been identified and approved by management. |
NT |
NT |
|
|
|
FISCAM SC-3.1 |
The Information Assurance Proponent contingency plan has been approved by key affected parties. |
NT |
NT |
|
|
|
FISCAM SC-3.1 |
Contingency plan responsibilities have been assigned. |
NT |
NT |
|
|
|
FISCAM SC-3.1 |
The Information Assurance Proponent’s contingency plan details instructions and procedures for restoring operations. |
NT |
NT |
|
|
|
FISCAM SC-3.1 NIST SP 800-18 |
The Information Assurance Proponent maintains an alternate processing site as part of its contingency planning. |
NT |
NT |
||
|
NIST SP 800-18 |
The location of stored backups is identified. |
NT |
NT |
|
|
|
FISCAM SC-2.1 |
The Information Assurance Proponent creates backups on a prescribed basis and rotates backups to an off-site location to avoid disruption if current files are damaged. |
NT |
NT |
|
|
|
FISCAM SC-2.1 |
Copies of system and application documentation are maintained at the off-site location. |
NT |
NT |
|
|
|
FISCAM SC-3.1 |
System defaults are reset after restoration from a backup. |
NT |
NT |
|
|
|
FISCAM SC-2.1 |
The Information Assurance Proponent backup storage sites and alternate sites are geographically separated and protected. |
NT |
NT |
|
|
|
FISCAM SC-3.1 |
The Information Assurance Proponent contingency plan has been distributed to all appropriate personnel. |
NT |
NT |
|
|
|
FISCAM SC-3.1 |
An updated copy of the Information Assurance Proponent contingency plan is maintained securely off-site. |
NT |
NT |
|
|
|
FISCAM SC-2.3 NIST SP 800-18 |
Personnel are trained in their responsibilities in the implementation of the Information Assurance Proponent contingency plan. |
NT |
NT |
||
|
FISCAM SC-3.1 NIST SP 800-18 |
The Information Assurance Proponent contingency plan is tested periodically and adjusted as appropriate. |
NT |
NT |
||
|
|
HARDWARE AND SYSTEM SOFTWARE MAINTENANCE |
|
|
|
|
|
FISCAM SS-3.1 NIST SP 800-18 |
The Information Assurance Proponent applies appropriate restrictions on who may perform maintenance and repair activities. |
M |
M |
||
|
FISCAM CC-3.2 FISCAM CC 3.3 |
Access to Information Assurance Proponent program libraries is controlled and restricted. |
M |
M |
||
|
NIST SP 800-18 |
Off-site and on-site maintenance procedures are in place, including escort of outsource maintenance personnel and necessary sanitization |
M |
M |
||
|
FISCAM SS-1.2 |
The Information Assurance Proponent operating system is configured to prevent circumvention of the security software and application controls. |
M |
M |
|
|
|
FISCAM SS-2.1 |
Updated procedures are in place for using and monitoring use of system utilities. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Impact analysis is conducted to determine the effect of proposed changes on existing security controls, including the required training needed to implement the control. |
NT |
NT |
|
|
|
FISCAM SS 3.1 FISCAM SS-3.2 FISCAM CC-2.1 NIST SP 800-18 |
System components are tested, document and approved prior to implementation. |
NT |
NT |
|
|
|
FISCAM CC-1.2 NIST SP 800-18 |
Software change request forms are used to document requests and related approvals. |
NT |
NT |
||
|
FISCAM CC-2.1 |
Detailed specifications are prepared and reviewed by management as part of change requests. |
NT |
NT |
||
|
NIST SP 800-18 |
The type of test data to be used is specified. |
NT |
NT |
|
|
|
FISCAM CC-2.3 |
The Information Assurance Proponent provides software distribution implementation orders, including effective date, to all effected locations. |
NT |
NT |
|
|
|
FISCAM CC-3.1 NIST SP 800-18 |
The Information Assurance Proponent employs version control for software changes, including proper labeling and inventory. |
NT |
NT |
||
|
FISCAM SS-3.2 |
The Information Assurance Proponent documents and reviews distribution and implementation of new or revised software. |
NT |
NT |
|
|
|
FISCAM CC-2.2 |
Emergency change procedures are documented and approved by management. |
NT |
NT |
|
|
|
FISCAM SC-2.1 NIST SP 800-18 |
Contingency plans and other documentation are updated to reflect system changes. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent documents and controls the use of all copyrighted software, shareware and equipment. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent system is reviewed periodically to identify, and eliminate when possible, unnecessary services. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent’s systems are periodically reviewed for known vulnerabilities and software patches are promptly installed. |
NT |
NT |
|
|
|
|
DATA INTEGRITY |
|
|
|
|
|
NIST SP 800-18 |
Information Assurance Proponent updates virus signature file on a routine basis. |
M |
M |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent conducts routine and automatic virus scans. |
M |
M |
|
|
|
FISCAM SS-2.2 |
Information Assurance Proponent routinely investigates inappropriate or unusual activity and takes appropriate actions. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent maintains procedures to determine compliance with password policies. |
NT |
PM |
|
|
|
NIST SP 800-18 |
Integrity verification programs are employed by applications to detect evidence of data tampering, errors and omissions. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Intrusion detection tools are installed on the Information Assurance Proponent system, and reports are routinely reviewed for suspected incidents. |
M |
M |
|
|
|
NIST SP 800-18 |
System performance logs are regularly reviewed and analyzed to determine availability problems and active attacks. |
NT |
NT |
||
|
NIST SP 800-18 |
Information Assurance Proponent performs penetration testing on its system. |
M |
M |
This project |
|
|
NIST SP 800-18 |
Information Assurance Proponent employs message authentication. |
NT |
NT |
|
|
|
|
DOCUMENTATION |
|
|
|
|
|
NIST SP 800-18 |
Information Assurance Proponent maintains vendor-supplied documentation of purchased hardware. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent maintains application documentation for in-house applications. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent maintains network diagrams and documentation on setups of routers and switches. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent documents and maintains software and hardware testing procedures and results. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent maintains standard operating procedures relating to how hardware and software is to be used. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent documents and maintains emergency procedures. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent documents and maintains backup procedures. |
NT |
NT |
|
|
|
FISCAM SP-2.1 NIST SP 800-18 |
Information Assurance Proponent documents and maintains a system security plan. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent documents and maintains a contingency plan. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent documents and maintains written agreements regarding shared data in interconnected systems. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent documents and maintains risk assessment reports. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Information Assurance Proponent maintains certification and accreditation, and authorize processing documents. |
NT |
NT |
|
|
|
|
SECURITY AWARENESS, TRAINING, AND EDUCATION |
|
|
|
|
|
NIST SP 800-18 |
All personnel have received a copy of their relevant Rules of Behavior. |
NT |
NT |
|
|
|
FISCAM SP-4.2 |
Employee training and professional development is documented and monitored. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent employs methods to make personnel aware of security. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent personnel have easy access to security policies and procedures |
NT |
NT |
|
|
|
|
INCIDENT RESPONSE CAPABILITY |
|
|
|
|
|
FISCAM SP-3.4 NIST SP 800-18 |
The Information Assurance Proponent maintains a written formal incident response plan. |
PM |
NT |
|
|
|
FISCAM SP-3.4 NIST SP 800-18 |
The Information Assurance Proponent maintains a process for reporting incidents. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Incidents are monitored and tracked until resolved. |
NT |
NT |
|
|
|
FISCAM SP-3.4 NIST SP 800-18 |
Personnel are trained to recognize and respond to incidents. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Alerts/advisories are received and responded to. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Following an incident, Information Assurance Proponent reviews incident handling procedures and control techniques for modification as appropriate. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Incident information and common vulnerabilities or threats is shared with owners of interconnected systems as appropriate. |
NT |
NT |
|
|
|
|
|
|
|
|
|
|
|
TECHNICAL CONTROLS |
|
|
|
|
|
FISCAM AC-2 NIST SP 800-18 |
Information Assurance Proponent maintains a current list of approved authorized users and their access. |
M |
M |
|
|
|
NIST SP 800-18 |
Access scripts with embedded password are prohibited. |
NT |
NT |
|
|
|
FISCAM AC-2.2 |
Information Assurance Proponent strictly controls emergency or temporary access. |
NT |
NT |
|
|
|
FISCAM AC-3.2 |
Personnel files are matched with user accounts to ensure terminated or transferred personnel do not maintain user access. |
M |
PM |
|
|
|
FISCAM AC-3.2 |
Passwords are changed at least every ninety days, or sooner if needed. |
NT |
NT |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
Information Assurance Proponent maintains password requirements to ensure security. |
M |
M |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
Inactive user accounts are disabled after a period of time. |
M |
PM |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
Passwords are not displayed when entered. |
M |
M |
||
|
NIST SP 800-18 |
Passwords are distributed securely and personnel are informed not to share their password with any other individual. |
M |
M |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
Passwords are transmitted and stored using secure protocols |
M |
M |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
Vendor-supplied passwords are eliminated and replaced immediately. |
M |
M |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
The Information Assurance Proponent maintains a limit to the number of invalid access attempts that may occur for a given user. |
M |
M |
||
|
FISCAM AC-2.1 |
Data owners periodically review access authorizations to determine whether they remain appropriate. |
M |
M |
|
|
|
LOGICAL ACCESS CONTROLS |
|||||
|
FISCAM AC-3.2 NIST SP 800-18 |
The Information Assurance Proponent’s security controls detect unauthorized access attempts. |
M |
M |
||
|
FISCAM AC-3.2 |
The Information Assurance Proponent’s access security software is restricted to security administrators. |
M |
M |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
The Information Assurance Proponent’s access control software prevents a single individual from having all necessary authority or information access to allow fraudulent activity without collusion. |
NT |
NT |
||
|
FISCAM AC-4 |
Access is monitored to identify and investigate apparent security violations. |
M |
M |
|
|
|
FISCAM AC-3.2 NIST SP 800-18 |
The Information Assurance Proponent’s workstations either disconnect or lock after a specified period of inactivity. |
NT |
NT |
||
|
FISCAM AC-3.2 NIST SP 800-18 |
Internal security labels are used to control access to specific information types or files. |
NT |
NT |
||
|
FISCAM AC-3.2 |
Communication software has been implemented to restrict access through specific terminals. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent maintains controls to restrict remote access to the system. |
NT |
NT |
|
|
|
FISCAM AC-3.2 |
Network activity logs are maintained and reviewed. |
NT |
NT |
|
|
|
FISCAM AC-3.2 |
Network connections automatically disconnect at the end of a session. |
NT |
NT |
|
|
|
FISCAM AC-3.2 |
Dial-in access is monitored. |
NT |
NT |
|
|
|
FISCAM AC-3.2 |
Access to telecommunications hardware and facilities is restricted and monitored. |
M |
M |
|
|
|
NISTSP 800-18 |
Firewalls or secure gateways are installed. |
M |
M |
|
|
|
FISCAM AC-3.2 |
Firewalls comply with firewall policy and rules. |
M |
M |
|
|
|
FISCAM AC-3.2 NIST SP 800-18 |
The Information Assurance Proponent maintains a standard log-on banner designed to appropriately warn unauthorized users. |
M |
M |
|
|
|
FISCAM AC-3.2 |
Access to tables defining network options, resources and operator profiles is restricted. |
NA |
NA |
|
|
|
OMB-99-18 |
The Information Assurance Proponent privacy policy is posted on the Information Assurance Proponent web site. |
NT |
NT |
|
|
|
|
AUDIT TRAILS |
|
|
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent audit trail provides a trace of user actions. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent audit trail supports after-the-fact investigations of system disruption chronology. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Access to online audit logs is strictly controlled. |
M |
M |
|
|
|
NISTSP 800-18 |
Information Assurance Proponent maintains a separation of duties between security personnel who administer the access control function and personnel who administer the audit trail. |
NT |
NT |
|
|
|
NIST SP 800-18 |
The Information Assurance Proponent reviews audit trails frequently. |
NT |
NT |
|
|
|
NIST SP 800-18 |
Automated tools are used to review audit records in real time or near real time. |
NT |
NT |
|
|
|
FISCAM AC-4.3 |
The Information Assurance Proponent investigates suspicious activity and takes appropriate action |
NT |
NT |
|
|
|
NIST SP 800-18 |
Whenever keystroke monitoring is employed, users are so notified. |
NA |
NA |
|
|
APPENDIX C RFA Draft Final Report
DRAFT
9 March 2003
RFA and RFE/RL Mutual Probe Report
In January 2003, Radio Free Asia and Radio Free Europe/Radio Liberty held a mutual network "probe" – testing vulnerabilities to various sorts of network attacks. While an educational exercise, many of the lessons learned were of the "how to do it better next time" variety, as opposed to successful penetrations. This should not be construed as a high score for security – while there were no significant exploits, the efforts were rudimentary. This stems from the fact that the average Network Administrator is more fluent in defense than offense. Becoming fluent in the tricks of the hacker trade is not something one typically does in one month, and in RFA’s case, travel and other job-related commitments cut into this effort significantly. Additionally, there was much confusion on which machines, IP ranges and sites were involved in this test. Nevertheless, some tools were explored, and some promising avenues raised at least as to a more thorough testing of network defenses. Below follows a description of basic results and approaches.
To start with, there were 2 presumed exploits found in remote systems. One was an open "test" account on an ftp server (rfeftp). The second was an IIS 5.0 server (alamo) reportedly open to the remote printing shell exploit. However, in the latter case, the supposed successful upload of data using the "jill" program did not upload the file (at least by file’s name). Some testing would be required to find out if the server was inaccurately represented as having a hole, or whether the exploit program did not work as advertised.
Some of the tools available for network testing included nmap, nessus, nbtscan, fragroute, brutus, nikto, vomit, et al. Some of these had difficulties with use from within a firewall, and due to time limitations, most were not successfully configured for testing purposes. Information gained from nmap scans led to categorizing a variety of systems publically available – packages and systems including Lotus, Eudora, Communigate, IIS, Apache, Cisco, Terminal Services, and a variety of open ports. Robustly categorizing and attempting possible exploits on these systems was not feasible at this time, though would be very useful to do.
Other useful tests would be actively testing from within the LAN to see what lies open. Disgruntled workers can be a source of much mischief, and knowing what vulnerabilities are present if an intruder passes the firewall is needed. Aside from this, user and maintenance dial-ins can be more weakly protected than internet firewalls, and in a real exploit, intrusion counts no matter what form the access takes.
From RFA’s defensive side, very little was required to prepare for the probe – fixing one Cisco box’s SNMP and VLAN parameters, disabling a few old generic accounts and turning off a couple of unneeded services on a Linux box. That said, it is again presumed that the serious hacker hobbyist would have more insight into exploits, and more time spent in the future learning some of these skills would provide more assurance that defenses are indeed solid.
In summary, the Mutual Probe while initially a bit weak seems to be a good candidate for a repeat exercise, perhaps with modifications to make it more thorough, informative and assured. While the probe is sometimes seen as an extracurricular activity, it is an opportunity for a planned investigation of outstanding security issues that normally does not happen due to typical workloads and crisis handling.
William M. Eldridge
Director Technical Development
Radio Free Asia
APPENDIX D RFE/RL Final Report
This report to be supplied
APPENDIX E SAMPLE Penetration Test Plan Document
During the course of the MISST&E the test facilitators were asked by the RFE/RL staff to produce a Sample Penetration Test Plan. This plan is included herein as a reference document.
Division of Information Resource Management
PENETRATION TEST PLAN
November 2002
Version 0.069
Submitted to:
Federal Deposit Insurance CorporationSample Organization
3501 1000 North Fairfax Sample Drive, Room VS42352
Arlington, Virginia 22226-350007
Submitted by:
MAXIMUSCONSULTANT

DRAFT FOR REVIEW ONLY
TABLE OF CONTENTS
1 Overview *
2 Methodology *
3 Objectives *
4 Network Description *
5 Test Requirements *
6 Test Performance *
7 Procedures *
8 Network Penetration Test Approach *
8.1 Work Plan Development. *
8.2 Test Tools. *
8.3 Black Box Testing *
8.3.1 Technical Information Gathering. *
8.3.2 System Penetration. *
8.3.3 Dial-In Testing *
8.3.4 Wi-Fi Test *
8.4 Identification of Critical Operations and Information. *
8.5 Gray Box Testing *
8.5.1 Technical Information Gathering *
8.5.2 System Evaluation *
8.5.3 Application and Service Exploits *
8.5.4 Telephone System Testing *
8.6 Vulnerability Report *
8.6.1 Identification and Analysis of Threat Environment. *
8.6.2 Vulnerability Analysis. *
8.6.3 Development of Protective Measures and Recommendations. *
8.6.4 Risk and Cost Benefit Analysis. *
8.6.5 Implementation of Selected Protective Measures. *
8.6.6 Vulnerability Report Guidance *
8.7 Conclusion: *
1 Overview 3
2 Methodology 3
3 Objectives 4
4 Network Description 6
5 Test Requirements 6
6 Test Performance 8
7 Procedures 8
8 Network Penetration Test Approach 9
8.1 Work Plan Development. 9
8.2 Test Tools. 9
8.3 Black Box Testing 11
8.3.1 Technical Information Gathering. 11
8.3.2 System Penetration. 12
8.3.3 Dial-In Testing 14
8.3.4 Wi-Fi Test 15
8.4 Identification of Critical Operations and Information. 15
8.5 Grey Box Testing 16
8.5.2 Telephone System Testing 20
8.6 Vulnerability Report 20
8.6.1 Identification and Analysis of Threats. 20
8.6.2 Vulnerability Analysis. 20
8.6.3 Development of Protective Measures and Recommendations. 21
8.6.4 Risk and Cost Benefit Analysis. 21
8.6.5 Implementation of Selected Protective Measures. 21
8.6.6 NIST Guidance 21
8.7 Conclusion: 22
TABLE OF FIGURES
Figure 1 Information Assurance Functional Spectrum. *
Figure 2 Concentric Barriers of Protection. *
Figure 3 FDICSO Network Overview *
Figure 4 FDICSO Information Assurance Overview *
APPENDICES
The purpose of this document is to document, describe and source requirements for the Federal Deposit Insurance Corporation (FDIC)SAMPLE ORGANIZATION (SO) Penetration Test Plan. The intent of penetration vulnerability testing is to assure adequate external protection is provided for all information collected, processed, transmitted, stored, or disseminated by FDICSO. The sensitivity of the FDICSO information systems is derived from levels of concern for the confidentiality, integrity, and availability of the information in the system for all FDICSO purposes.
The evolution of global, integrated networks has significantly increased the threat to critical IT assets. Unfortunately, the accelerating rate of technology development, and the resulting increase in threats to critical assets, has outpaced the ability of most organizations to protect their information systems from the wide range of threats that they face today. To understand how we approach penetration and vulnerability testing, one needs to understand the FDICSO requirements for protecting information.
The purpose of the FDICSO Penetration Test is to ensure that the required security safeguards are in place to protect FDICSO’s Information Technology (IT) assets against unauthorized modifications, disclosure, destruction, and denial of service attacks throughout all of the systems’ life cycles and to ensure the confidentiality, integrity, and availability of these assets. The requirements limiting the level of FDICSO public system exposure establishes the parameters for FDICSO Penetration Test procedure.
The FDICSO's Information Assurance (IA) Program is based on requirements driven risk mitigation methodologies and technologies. The FDICSO maintains a number of innovative tools from across the information security industry, to augment our assurance program. The FDICSO IA approaches are consistent with the standards of the National Institute of Standards and Technology (NIST), National Security Agency (NSA), Carnegie Mellon University, and with industry best practices of information technology auditing (such as Control Objectives for Information and Related Technology (CobiT)). This methodology and associated tools have proven to be successful in protecting FDICSO business and technical systems through a systematic and flexible approach to problem resolution and risk mitigation. While the FDICSO is not a recognized leader in information technology management, the (Department of Infromation Resource Management, Office of the Chief Information Officer (DIRM OCIO) office provides a value-based approach that includes executive-level participation in risk awareness, as well as mitigation and acceptance of residual risk.
The primary directive of the penetration and vulnerability test is to ensure computer systems and network operations will not be intentionally interrupted. Extreme care will be exercised to ensure that network availability and data integrity are in no way compromised. User data will neither be destroyed nor corrupted. In order to further prevent operational risk, FDICSO technical representatives will be informed of serious security shortcomings that should be corrected immediately.
The test methodology will include initial "Black Box" testing, where disclosed technical information gathering is strictly limited, and "Grey Box" testing which takes place in a disclosed internal arena. In either case the objective is to test for user, root or administrator access, system penetration including wireless and dial-in attacks.
Thus, in testing for potential vulnerabilities, the FDICSO expects the Penetration Team to use a dual (black box/gray box) methodology that captures the security and vulnerabilities of the network system as a series of snapshots in time by, typically, fielding two teams of security vulnerability specialists. The "unknowledgeable" team represents unauthorized persons who are not familiar with the infrastructure and content of FDICSO systems. This team will initiate their "black box" attacks first. The knowledgableknowledgeable gray team follows and simulates a trusted attack.
This dual methodology continues by following the attack by an external threat with an internal threat, such as could be attempted by trusted individuals who are more knowledgeable about FDICSO computer systems and networks. The penetration team follows this "gray box" test process, performing discovery, planning, invasion, and operations starting from the inside network, and working down to the database-level. This gray box team will perform a battery of penetration tests on the internal systems at various times to attempt to exploit weaknesses. No denial No denial of service attacks will be used.
The most important premise the penetration test test considers as they carry as they carry out their tasks is to understand and protect the business of the FDICSO. The fact is that SECURITY IS A FUNCTION OF BUSINESS. This basic understanding is important to the fundamental objectives and mission of the organization when performing security testing. In reviewing IT security requirements, we know that both proactive countermeasures and reactive functions must be included in an acceptable protection program. Figure 1 depicts a sampling of this information assurance spectrum whereby the health of an organization is also reflected by its depth of integrating into its policies a "tooth-to-tail" solution.
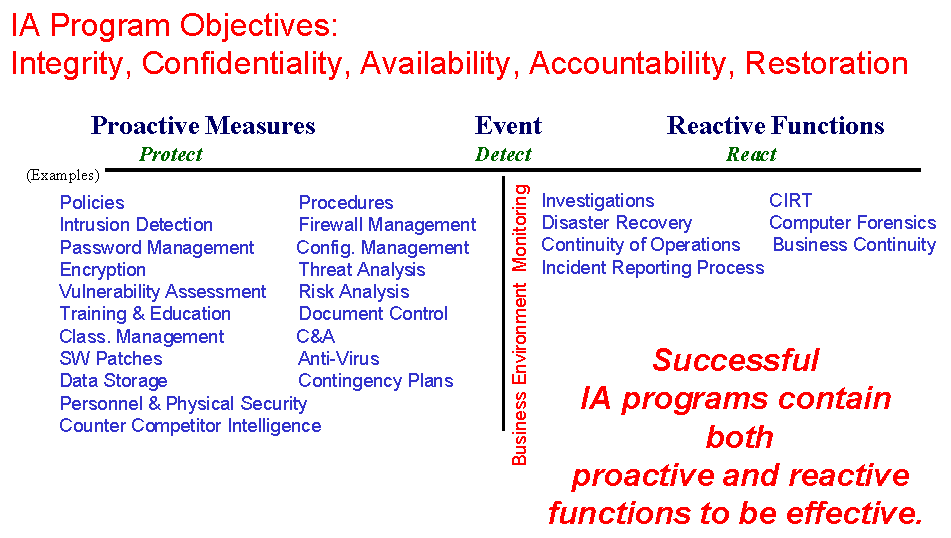
Figure 3 Information Assurance Functional Spectrum.Spectrum.
Proactive measures mitigate many IT security risks. Reactive measures can aid in eliminating future risks. Both proactive and reactive actions protect critical assets, information and systems. These are represented as layers in the Figure 2.
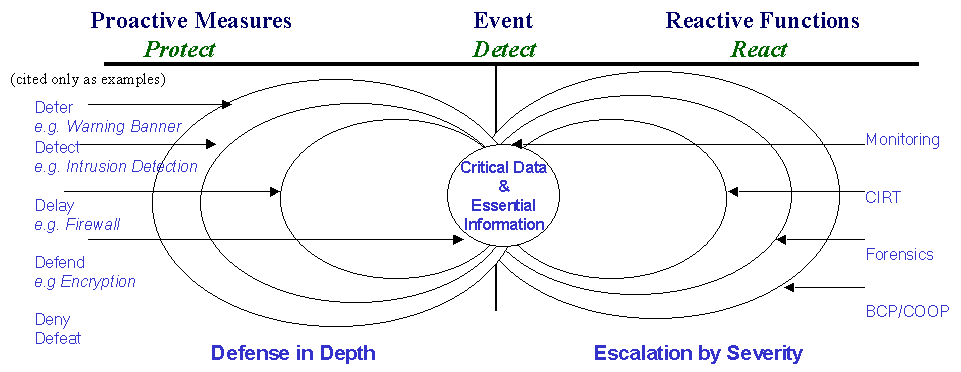
Figure 4 Concentric Barriers of Protection.
Thus, managing the risk from multiple threats to FDICSO systems requires a structured requirements driven methodology.
The FDICSO Network is composed of the Virginia Square and Dallas Texas ATM internetworks inside FDICSO’s security perimeter. This "inside" network is demarcated with firewalls and protected by Network Intrusion Detection Systems (NIDs).(NIDs). The interior FDICSO Network is sited within the Virginia Square, Arlington, Virginia and Dallas, Texas, FDICSO buildings respectively. Both sites enjoy an Internet Point of Presence (POP) provided by local Internet Service Providers (ISP). FDICSO staff and contractors administer this protected ATM network, and control all the backbone equipment on this network. Figure 3 depicts this network.
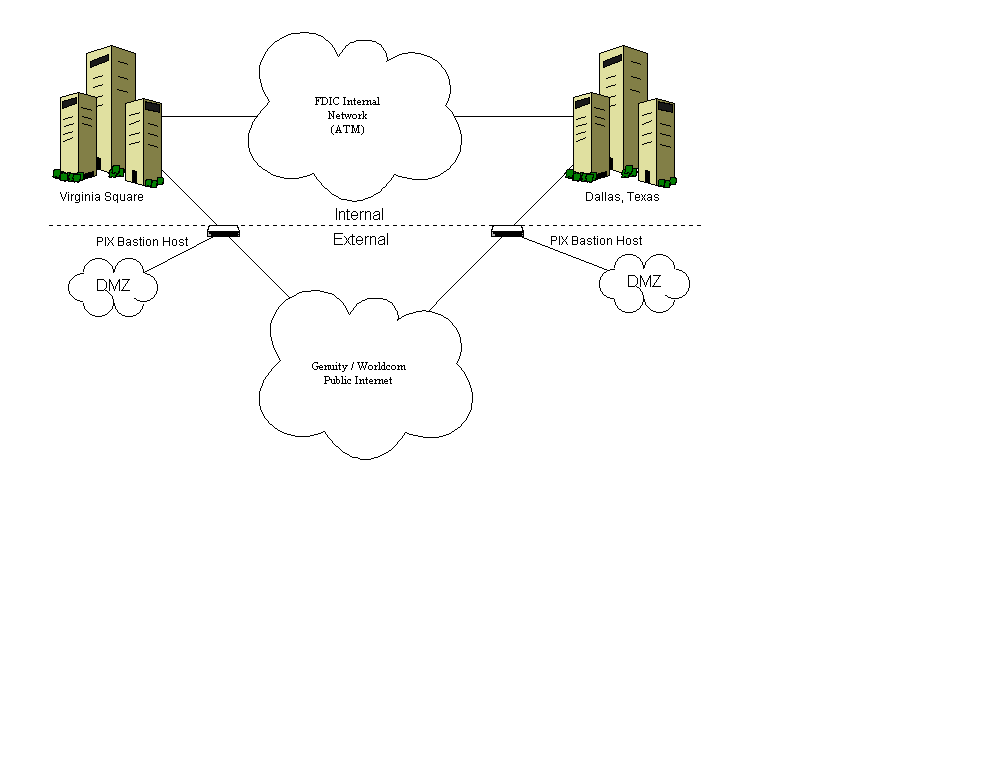
Figure 5 FDICSO Network Overview
This section defines traces, delineates and demarcates the basis for the Penetration Test discussed in the procedures section which immediately follows.
The overriding FDICSO test requirement is to ensure that all information systems within FDICSO control have a level of security that is commensurate with the risk and magnitude of harm that could result from loss, misuse, disclosure, or modification of the information contained in the system.
Additional security test requirements can be found in the FDIC Security Requirements Matrix (SRM) which should accompany this test planning document. These requirements are the derived from Law, Policy, Guidance, Best Practice, Rules and Regulations as shown in Figure 4. Additional security test requirements can be found in the SO Security Requirements Matrix (SRM) which should accompany this test-planning document. These requirements are the derived from Law, Policy, Guidance, Best Practice, Rules and Regulations as shown in Figure 4.
Figure 6 FDICSO Information Assurance Overview
The purpose of penetration testing is to validate that the controls defined to minimize threats and mitigate vulnerabilities are adequate and capable of supporting these derived requirements.
The tangible and deliverable goal of this penetration test exercise is the Vulnerability Report, which will will be analyzed and become part of the Risk Assessment document, which ultimately directs modification of the security controls of the FDICSO IA activity, as shown in Figure 4.
The risk to these systems by criminal exploitation, attack, malware, or other forms of misbehavior, and the data they carry requires the evaluation and test of the organization’s computing capability to mitigate damage or loss of FDICSO information or assets. Network penetration testing is a major component of assessing the vulnerabilities of IT systems and their operating environments, and is a critical cornerstone to IT governance for adequately managing risk, performance, data privacy, and security. The FDICSO is challenged to ensure data integrity, confidentiality, and systems availability across a large and complex computing infrastructure.
The FDICSO seeks assistance in investigating system vulnerabilities, possible misconfigurations, malware identification, risks to FDICSO data and exploitable paths to FDICSO information. The FDICSO understands that this inspection is a ‘snapshots-in-time’ that will establish a benchmark for the FDICSO OCIO’s Cyber Security Program to develop corrective mitigation strategies and objectives for the near future associated with electronic threats and system vulnerabilities.
FDICSO representatives must be present to view both the black and gray ‘white hat’ attacks on FDICSO systems. In witnessing this FDICSO engineers and analysts will be sure to provide FDICSO management with a full understanding of test methods, techniques and tools used during each task. This knowledge transfer is essential to the FDICSO for sound reporting, CIRT coordination and effective countermeasures development.
In light of these constraints, the FDICSO's Office of the Chief Information Officer (OCIO)(OCIO) and the Cyber Security Program expect a group of information security specialists familiar with Information Assurance (IA) practice perform the vulnerability penetration test based upon the FDICSO SRM and submit a report on the vulnerability of the external and internal portions of the FDICSO network. This work will be conducted in order to gauge the strength of FDICSO's network in-depth defenses to meet the requirements derived from the Computer Security Act, OMB Circular A-130, the Privacy Act, the Government Information Security Reform Act (GISRA) and other regulatory mandates as stated in the FDICSO SRM.
Specific to the black testtest, the penetration teams shall assess the security perimeter of FDICSO networks. The development of protective countermeasures requires a multi-layered, defense-in-depth approach because only shutting down the FDICSO network can successfully mitigate all vulnerabilities and risks. It is expected that there are point solutions as well as infrastructure enhancements, and these often lack the integration required, providing further vulnerability for exploitation. The FDICSO is aware that the very nature of security (e.g. deter, detect, delay, defend, defeat, and deny criminal intentions or human error) is proactive and understands the need to attempt to penetrate and go around these protection mechanisms in order to validate them. The FDICSO uses the GSA FEDCIRC to support its internal and external networks. This reactive CIRC function is crucial to fulfilling the expectations of integrity, availability, confidentiality, accountability and restoration as a network security function. The FDICSO expects that the penetration team will work with the FEDCIRC as necessary to provide a total understanding of attempts, failures and successes in testing the assurance capabilities as required by FDICSO.
A kick-off meeting begins the planning of the types of activities whichactivities that will require a detailed requirements-based structure. This is followed by the development of a project work plan. The kick-off meeting will set performance expectations and legal boundaries, schedules and milestones. The kick-off meeting minutes and the draft work plan will be submitted for review, and testing will not commence until a final work plan is delivered and approved.
FDICSO provides its staff with global access to extensive databases or Centers of Excellence on systems benchmarking studies, best practice research, training tools and techniques, COTS evaluation, testing, and implementations, business process reengineering, and others which include:
Both penetration test teams will consult with FDICSO to use a combination of scanning products and methodologies to conduct a thorough scan for network vulnerabilities. Most importantly, our team will then use its extensive expertise to analyze the results of the scans to advise the agency of the risks associated with each vulnerability found, develop recommendations and countermeasures for corrective actions, estimate the level of effort required to implement corrective actions, and establish the priority of each action. Examples of tools used on past security diagnostic engagements are listed below.
Scanners Scanners
Scanners are programs that sequence through frequencies, IP addresses or port numbers looking for open connections. Examples inlcudeinclude:
Password Crackers
While this may seem outside the scope of this effort, this testing is necessary to assure our depth in capability and technical knowledge. knowledge.
Other tools to consider include but are not limited to:
The selection of tools to be used in FDICSO network testing will be based on industry and FDICSO staff confidence in the reliability of the tools. The FDICSO approach to testing is to use the best tools available for each type of system to aid in our analysis. FDICSO consideration should include CyberCop, a commercial tool that is strong in Unix, (particularly LINUX and Solaris) and reasonably good at Windows NT and Cisco routers. It has many false positives and reports the same vulnerabilities several ways.
Additionally the FDICSO should consider using several public domain tools including Sara, Netcat, NTcrack, Satan, and NMAP. These tools are good but should be deployed with care to avoid any systems problems
With the written permission from the FDICSO, for a period of performance not to exceed an estimated one month, the black test team will conduct a number of scans and probes of external FDICSO systems in an attempt to penetrate the network in a realistic simulation of external, unauthorized access. All penetration attempts will be documented and witnessed by FDICSO personnel. The results of this test and assessment will be included in the vulnerability report and provide to the FDICSO with specific counter measures recommendations.
The collection of publicly available information concerning a target network is a vital first step in penetration testing. A wealth of information about any public network is available via a series of internetworking system services as well as through use of information gathering tools. The types and importance of the information varies with each service and tool, but together this information can be used to determine highly probable points of success for surveying. This information can be as simple as host names and operating system versions listed in DNS (e.g., recently, a Sparc Station that carries the name sun0s42.FDICSO.gov or a router that carries the name cisco.FDICSO.gov). The information can, in some cases, be compiled to form educated guesses diagramming the trust relationships between systems and trust flow direction. Such public intelligence can be used in attacks on systems and applications and may be considered in the vulnerability report.
Physical network design and routing information can often be determined through use of Wi-Fi (wireless), Dialup or IP scan tools. Additionally, network basednetwork-based intelligence gathering through the use of SNMP Management Information Blocks (MIBs), or a routing protocol are possible avenues. This information can be used later by spoofing tools or other attack methods.
Thus supplied and equipped, the "black box box" penetration teams attack from the perimeter inward operating in phases as a "hacker" would; initiating probes, conducting Wi-Fi and Dial-Up exploitation, MIB collection, social engineering and any other technique which advances the assault. The operational goal of the black box tester in invading the network is to obtain and strengthen a position inside the network and continue to conduct intelligence gathering operations as long as possible before being detected or thwarted.
Once all possible information is gathered and examined, vulnerable systems on the exposed networks will be exploited. The methods used to gain system access will be selected from those that the analysts feel have the greatest potential for success and have the least potential for detection by monitoring services. Efforts will be directed towards gaining a shell account on a system physically located on the exposed portions of the network. Shell accounts are compromised using a variety of techniques and exploitation software. These techniques and software typically exploit known holes or "bugs" in many common services.
The test team will attempt to exploit as many known vulnerabilities of the computers, routers, firewalls, network operating systems, protocols, and other components as possible in the defined test period. In some cases, vulnerabilities of one or more components will be exploited to provide stepping-stones to exploit other components. For example, one might need to exploit Simple Mail Transfer Protocol (SMTP) vulnerabilities to gain access to a firewall system before monitoring traffic ("sniffing") for network addresses to select and compromise a host. Evidence of exploitation will be introduced, where plausible, to demonstrate the seriousness of the vulnerability. vulnerability.
This test team will likely perform an in-depth port scan of FDICSO’s internet perimeter checking for responsive hosts and accessible services (TCP, UDP and ICMP-based) and report those "High-Risk" and other services that are found running on the hosts and visible to the Internet. The test team will then seek to exploit these services. The penetration team will employ a variety of automated and commercially available tools to remotely probe the specified networks for security vulnerabilities determined as appropriate, recording vulnerabilities, configuration problems, and unnecessary services. The vulnerability testing can be expected to check for susceptibility to most or all of the following security holes, as well as others appropriate to the specific configurations:
There exists a wealth of system-specific attacks known to achieve a higher level of privilege within the net. Some common attacks are listed below.
Most of the system penetration and shell access attacks can be used to gain increased privilege once user-level access is achieved.
All passwords are encrypted, but the user IDs can now be viewed. Password "cracking" software can be run against the password file on compromised NT and Unix systems. Manual (brute force) password guessing may also be used particularly against appliances (e.g. routers and switches) to achieve increased system privileges.
Cron jobs are typically available for modification at the user level. Unpatched Crontab can be used to escalate privilege level. Cron jobs are typically available for modification at the user level. Unpatched Crontab can be used to escalate privilege level.
System logs as well as other publicly known system files can be exploited to gain intelligence and escalate privilege level.
"Kiddie Scripts""Kiddie Scripts" are scripts and actual compiled code to employ more advanced exploits of specific known security flaws. Most of these make use of software "bugs" that fail to protect memory isolation. An example of such a "bug" is a buffer overflow condition that allows the analyst to overwrite instruction pointers and execute code.
Where active administration is apparent, techniques will be used to attempt to hide test team presence and the history of intrusion. These tools typically attempt to bypass monitoring programs and DLLs such as ps, ls, sum, and who. Where required, we will leave non-disputable evidence of access on particular systems.
The black test team shall conduct testing of the FDIC dial-up services. Our understanding is that FDIC dial-up consists of 10-14 prefixes in the Arlington and Dallas LATAs. The test team will identify unsecured dial-in services throughout the internal network. To that end, the team will employ automated dialing software to scan entire exchanges. The software will log all results and identify all lines where a modem answers. A penetration team member will then manually dial each modem and determine if the authentication processes are strong enough to resist unauthorized access attempts. This testing could potentially lead to unauthorized access. Due care will be exercised to ensure that network availability and data integrity is in no way compromised. The purpose of these tests is to determine if any external party can gain unauthorized assess through remote means. The black test team shall conduct testing of the SO dial-up services. Our understanding is that SO dial-up consists of 10-14 prefixes in the Arlington and Dallas LATAs (Local Access Transport Area). The test team will identify unsecured dial-in services throughout the internal network. To that end, the team will employ automated dialing software to scan entire exchanges. The software will log all results and identify all lines where a modem answers. A penetration team member will then manually dial each modem and determine that the authentication processes are strong enough to resist unauthorized access attempts. This testing could potentially lead to unauthorized access. Due care will be exercised to ensure that network availability and data integrity is in no way compromised. The purpose of these tests is to determine if any external party can gain unauthorized assess through remote means.
Recent advances in radio based networks, particularly but NOT limited to the Wi-Fi (IEE 802.11 standard) have caused prices to drop and availability of wireless technology to blossom in the data processing area. Examples of wireless systems abound, and include:
As well as a plethora of proprietary radio and optical links.
Regardless of what the current operational posture towards this technology is, it is necessary to survey both physical sites and determine the extent that formal or informal use of this technology will breach the FDICSO security posture.
The principal tool used in this survey should be a Sharp Zaurus running Kismet, a scanner tool dedicated to this type of activity.
As a prelude to the "Gray Box" testing, the penetration test team will work with FDICSO staff to identify critical, sensitive data that may be involved with or resident on the systems to be tested. (E.g., financial, contracts/bid information, privacy-act data, patents, passwords, investigative data, etc.). This information will be used by the gray team to understand what information we may come in contact with in order to adequately protect and/or exploit it as directed by the FDICSO staff.
The information and methods used from the black (unknowledgeable) team will have demonstrated external vulnerability to outside threats. This data will be disclosed to the gray (knowledgeable) test team who, during their review of the internal configurations, will verify the penetration and will capture corrective actions to be identified in the vulnerability report. Any dangerous security vulnerabilities noted will be immediately brought to the attention of the FDICSO in a vulnerability memo.
The second team, the "knowledgeable" team represents persons who are knowledgeable about the content and infrastructure of FDICSO systems and may look to perform some unauthorized function, data manipulation, theft, or other misbehavior. This team represents both internal threats posed by employees, and potential external risks from previous employees or others outside FDICSO who may have become knowledgeable about certain aspects of the networks, architecture, and information.
The FDICSO gray box test penetration team will next perform as a ‘knowledgeable’ threat as directed by the FDICSO and within the scope of the Security Requirements Matrix. Gray Box testing will consist of probing the FDICSO perimeter defenses for vulnerabilities and attempting to penetrate security controls to attain user-level access, and ultimately, system-level control. It is our understanding that approximately 150 IP addresses and additional telephone prefixes are included in this initiative. It is understood that VM, MVX, Unix, Novell and NT operating systems are presently operational on the interior network. Analysts will scan and probe the FDICSO networks to discover and exploit vulnerabilities in an attempt to penetrate corporate systems both internally and externally from the Internet. The security testing performed in this task will be used to complete the vulnerability report in an effort and determine across the organization the security posture of the FDICSO’s information assets.
The knowledgeable team shall perform a series of vulnerability scans and configuration reviews of the networks. The tests will be conducted both internally and externally as knowledgeable individuals, with the distinction that these gray team members will detail the findings and report on and make recommendations of defensive countermeasures into the vulnerability report.
The testing shall include an extensive internal vulnerability assessment of the FDICSO external network. These tests will assess system vulnerabilities, exploitable mis-configuration and other potential security weaknesses as introduced from either an internal or an external source. The tools used will be as agreed in the Kick Off Meeting and assured free of malicious code. This penetration attempt will establish the protective, security posture of FDICSO from both internal and external threats. Some examples of the type of issues that to be called out and addressed during the perimeter evaluation are:
Potential attacks are based solely upon the targeted system’s active operating system services. Since operating systems and services control and configuration vary widely, exploitation requires an in-depth knowledge of the latest discovered security flaws of each operating system, as well as all system services. This information will have been gathered to as part of the specific methodology that will be used. However, some of the more common system attacks are itemized below.
Applications and services (e.g., mail and information publication) will be examined for weaknesses and design. The goal of the information-gathering step is to provide the team with enough information to be successful in penetrating the first system on the network. The following technical procedures will be performed to exploit open source data:
The commercial public and government InterNIC domain registry databases will be searched for entries referencing the target network. At a minimum, this search should result in the addresses of the network’s external DNS servers.
Public DNS addresses will be examined. This will provide us with named systems that are exposed, as well as potential inside systems if the DNS publication process is not discrete.
E-mail will be examined for Internet design and authority and for software that is being used. E-mail is also a classic source of exploitation through the use of Trojan horse programs.
Sendmail is commonly used to gain unauthorized access to a host system. The deamon software has a wide variety of known security flaws. Common attacks include writing to system files, and forcing the read and re-mailing of system files.
Insecure services such as NIS provide not only direct access to password files, but in some cases allow remote execution of privileged commands.
Host scanning will be used to identify active hosts that the test team can "see" from the Internet.
If present, TFTP can provide access to the password file.
NFS attacks are usually file based, and work via remote file system mounts. This is typically used to access mail or to exploit trust relationships (rlogin, rexec, rsh).
Mis-configured FTP servers can sometimes provide attack opportunities. These include file access attacks as well as rlogin/exec commands.
These servers over the past year have become well known for mis-configurations of CGI scripts, as well as bugs in the daemon software which allow remote execution and file access.
TCP and UDP ports will be randomly scanned on all "visible" hosts. The combination of this information and the previously gathered information will provide the team with knowledge of active system services and, to some degree, application interaction between exposed systems. These applications and system services will be examined to locate systems that are potentially vulnerable to attack.
Once determined to be open, the 65,636 available ports per IP address can be a sumptuous source of further intelligence about the FDICSO network. Venerable examples of this are the Finger Services, either port 79 or 2003. Finger data can be used to determine user account information and, in some cases, other traffic flow information.
Once a foothold is gained, these steps will be repeated from each compromised system so that levels of trust can be determined as well as to advance placement inside the network.
Once a shell account as a normal user is achieved, the penetration teams attention will turn to obtaining administrative privilege, which is tantamount to having total system and applications control (except perhaps to some databases). Also, once "root" access is achieved (in some systems, called Administrator or Supervisor), that system can often be used for a remote staging point for new attacks. Root access on most Unix-based systems, administrator on Windows NT-based systems and supervisor on Novel systems also provides the ability to place the network interface into promiscuous mode and capture remote network data and traffic. This is typically referred to as "sniffing".
Once sniffing capability has been achieved, attacks on remote systems become increasingly successful due to the increase in potential attacks and information gathering methods. Also, the ability to "sniff" the external network may provide clues as to what types of traffic are permitted through the firewall. The previous methodologies will continue to be used to gain access to systems located on the external network. If more than one external sub network exists, the methodology is repeated for each targeted sub network. In most cases, the same exploits used to gain user level access on a system can be used locally to gain root access. In addition, any and all configuration errors on the system may potentially be used to obtain privilege.
Additional telephone system features worthy of test include:
The operant factor here is to understand that the FDICSO Private Branch Exchange (PBX) is in reality merely a network attached computer in its own right, and that as an Automated Information System can be exploited with spectacular result.
Following an analysis of our findings and observations, The Penetration Teams will prepare a vulnerability report for submission to the Contracting Officer Technical Representative (COTR). Unless otherwise directed, this report will follow the OMB standards for reports and be presentable to the Inspectors General.Following an analysis of our findings and observations, The Penetration Teams will prepare a vulnerability report for submission to the Contracting Officer Technical Representative (COTR). Unless otherwise directed, this report will follow the OMB standards for reports and be presentable to the Inspectors General.
Threat analysis is extremely important in determining what risks are challenging FDICSO activities. Threat identification consists of determining internal and external threats that can introduce risk to the Agency. The penetration test teams are, in this phase, concentrating on vulnerability detection and analysis, and it is important to be aware of the threat environment. Of particular sensitivity are immediate threats to operational systems. However due to this assessment being limited to vulnerabilities, the FDICSO assumes that threat information will not be detailed, but rather a generic assumption of threat from both internal and external sources. Uunauthorized persons attempting to gain remote access to FDICSO systems will be the basic tenet to these vulnerability tests.
The penetration team will consider the FDICSO’s current operations and critical information then compare them against the cited vulnerabilities with an eye on the FDICSO requirements. Sensitive information that is unprotected, collectable or exploitable by vulnerability is subject to compromise and is, therefore, at risk. The analysis of the identified vulnerabilities is a necessary element within this step and could be cited within the risk analysis portion of the system certification and accreditation, GISRA review and OMB A-130 documentation. The test team thus takes great care that information collected during the penetration tests is input to a vulnerability report. This data can in turn be used in an automated risk analysis tool that will provide immediate or continuous risk assessment to aid in risk management, the NIACAP and return on control decision making.
While not part of the scope of the penetration testing process, cost-effective countermeasures are often researched and recommended to minimize each identified vulnerability. The test team security professionals possess extensive experience in developing innovative solutions that agency executives should consider. Ad hoc recommendations could include installing encryption devices, additional network monitoring, control, requirement, regulation or policy development.
Informal mitigation strategies, recommendations and protective measures will likely be accompanied with rough order of magnitude cost estimates. These can be prioritized and included in the vulnerability report. This is an area that, in accordance with the FDICSO’s risk management philosophy, budget, and timing might also be included in the formal risk assessment.
While not contemplated as part of this penetration testing effort, the FDICSO remains ready to implement these ad hoc recommendations, particularly on areas of critical concern, high risk or high visibility. These recommendations may include:
The vulnerability report will be written in accordance and in compliance with the
The lack of effective data integrity controls based upon stated requirements, can and does pose security vulnerability through inaccurate or missing data resulting from unauthorized destruction or tampering of electronic files and records. The vulnerability report resulting from the process outlined above can be developed into a plan allowing the FDICSO to assign appropriate resources, develop and implement action plans to fully meet data integrity requirements.